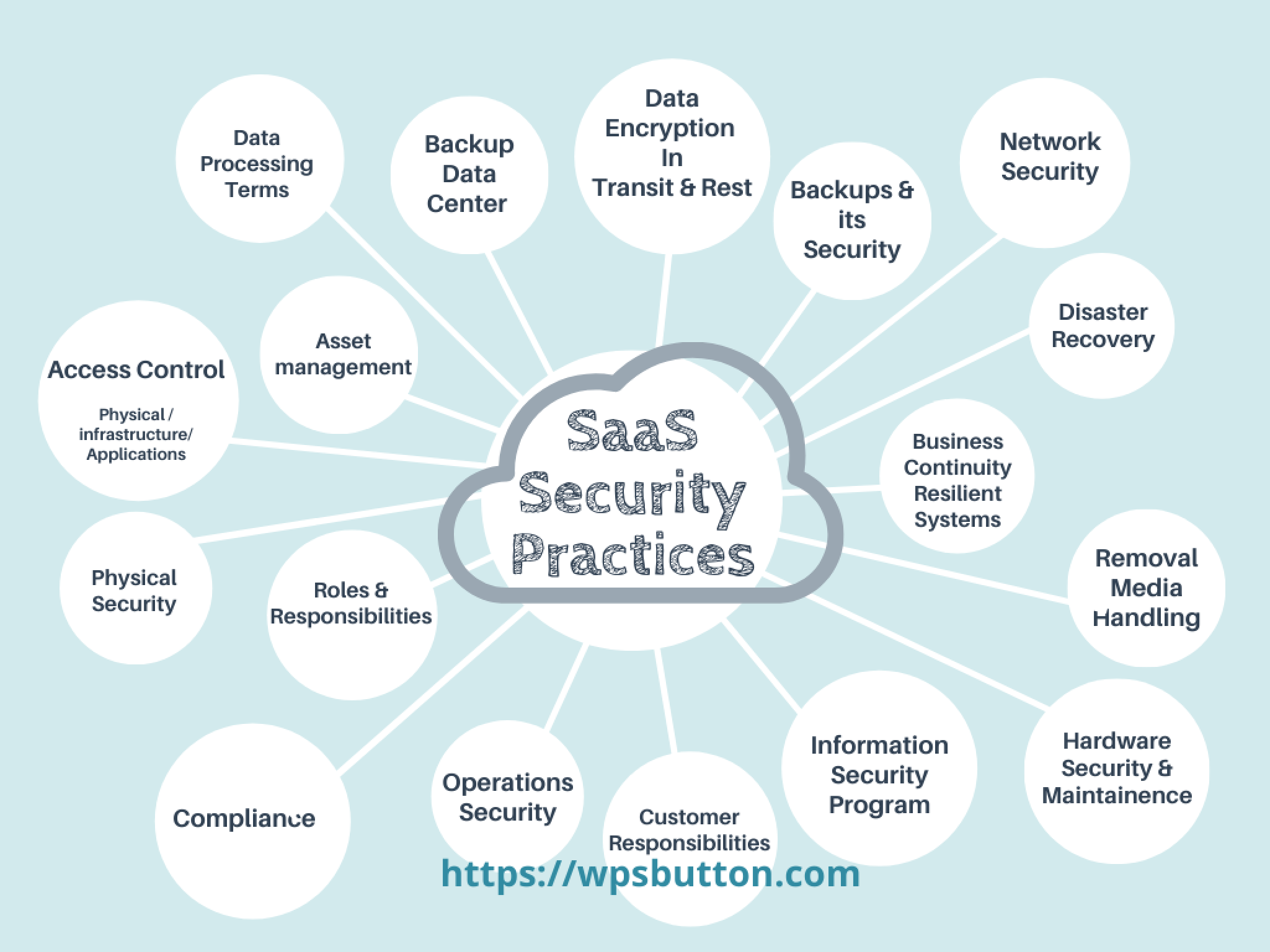
In today’s digital age, ensuring robust data security in the cloud is paramount for organizations of all sizes. With the increasing reliance on cloud services, the need for cloud service data security best practices has never been more critical. This ultimate guide dives deep into the essential strategies and techniques, such as encryption, IAM (Identity and Access Management), data backup, compliance, and more, that organizations can implement to safeguard their sensitive information. By empowering your workforce with the right knowledge and tools, you can enhance your security posture and mitigate risks effectively.

Understanding the Shared Responsibility Model in Cloud Data Security
In the realm of cloud data security best practices, understanding the shared responsibility model is paramount. This model delineates the distribution of security duties between cloud providers and customers. While cloud providers safeguard the infrastructure, customers bear the onus of securing their data and applications. By grasping this model, organizations can allocate resources efficiently, mitigating risks by delineating clear roles and ensuring accountability to prevent security vulnerabilities and address potential gaps effectively.

Mastering Identity and Access Management: Enhancing Cloud Data Security
Understanding IAM Systems for Enhanced Security
Identity and access management (IAM) systems are pivotal in governing access to cloud resources, dictating user privileges and actions within the cloud environment. These systems grant organizations the power to delineate user roles, assign specific permissions, and establish stringent access policies. By leveraging IAM features, businesses can ensure that only authorized personnel access sensitive data, bolstering overall cloud data security.
Implementing Robust IAM Practices for Data Protection
Organizations benefit from the comprehensive IAM capabilities offered by cloud providers, enabling them to set up detailed user roles, fine-tune permissions, and enforce strict access control measures. Such robust IAM implementations serve as a critical layer of defense, significantly lowering the likelihood of unauthorized entry and thwarting potential data breaches. Securing user permissions through IAM is fundamental in fortifying cloud data security frameworks.
Ensuring Ongoing Security with Regular IAM Reviews
A proactive approach to cloud security involves consistently reviewing and auditing IAM configurations to identify potential vulnerabilities and ensure compliance with security protocols. These routine assessments play a vital role in detecting and mitigating emerging threats, safeguarding against privilege escalation, and maintaining the integrity of user permissions. Regular evaluations of IAM settings are essential in upholding robust cloud data security best practices.
By emphasizing the importance of IAM systems in controlling user permissions within cloud environments, organizations can fortify their overall security posture, mitigate risks associated with unauthorized access, and uphold the confidentiality and integrity of their sensitive data. Combining granular IAM features with regular audits offers a proactive defense mechanism that strengthens cloud data security best practices, paving the way for a secure and resilient digital infrastructure.

Enhancing Cloud Data Security Through Vigilant Monitoring and Strategic Incident Response
Continuous Monitoring for Timely Threat Detection
To sustain robust cloud data security best practices, organizations must prioritize continuous monitoring to swiftly identify and address security threats. Constant surveillance allows for proactive threat detection, enabling timely response and mitigation strategies to safeguard sensitive data effectively.
Leveraging Cloud Provider Monitoring Tools for Real-time Insights
Cloud service providers offer advanced monitoring tools and services that furnish real-time visibility into cloud activities. By leveraging these resources, organizations can gain valuable insights, monitor network traffic, and detect abnormal behavior promptly, enhancing overall security monitoring and incident response capabilities.
Crafting Effective Incident Response Plans
Establishing comprehensive incident response plans is pivotal in cloud data security best practices. These well-defined protocols outline the precise steps to follow in the event of a security breach or incident, ensuring a structured and efficient response that minimizes potential damages and facilitates swift resolution.
Strengthening Security through Audits and Penetration Testing
Regular security audits and penetration testing play a vital role in fortifying cloud data security. These practices help identify vulnerabilities, assess the efficacy of existing security measures, and enhance the overall security posture. By conducting thorough assessments, organizations can proactively mitigate risks and bolster their defense mechanisms against potential threats.
Incorporating these practices into your cloud security strategy empowers organizations to proactively safeguard their data, respond effectively to security incidents, and continually enhance their security posture to align with industry best practices in Cloud Data Security.

Empowering Your Workforce through Education and Training
Educating employees on Cloud Data Security Best Practices is crucial to minimize human errors and thwart security breaches. By instilling a culture of awareness and responsibility, organizations can create a more secure environment.
Cloud service providers furnish training initiatives and tools to assist in fostering a workforce knowledgeable in security practices. Leveraging these resources can significantly enhance your organization’s security posture.
Training sessions should encompass essential areas like data safeguarding, user access control, and protocols for responding to security incidents. Equipping employees with this knowledge is pivotal in fortifying your overall security strategy.
Consistent security awareness campaigns are fundamental to keeping staff updated on emerging threats. By promoting a culture of vigilance and proactiveness, organizations can effectively mitigate risks and fortify their defense against potential security breaches.