In the ever-evolving landscape of cloud computing, ensuring robust data protection is paramount. The Ultimate Guide to Cloud Service Data Protection delves into the intricacies of safeguarding sensitive information stored in cloud environments. From discussing key elements such as encryption and access controls to exploring best practices and compliance regulations, this guide offers a comprehensive overview to help you fortify your data security measures. Stay ahead of emerging trends and enhance your understanding of Cloud service data protection to mitigate risks effectively.
As businesses increasingly rely on cloud services to store and process data, the need for stringent data protection measures has never been more critical. Cloud service data protection encompasses a range of practices and regulations aimed at safeguarding data integrity and confidentiality. By implementing robust security protocols and adhering to compliance standards, organizations can secure their data assets against unauthorized access and data breaches. Stay tuned to uncover essential insights and expert recommendations to fortify your data protection strategies and maintain compliance in cloud computing environments.
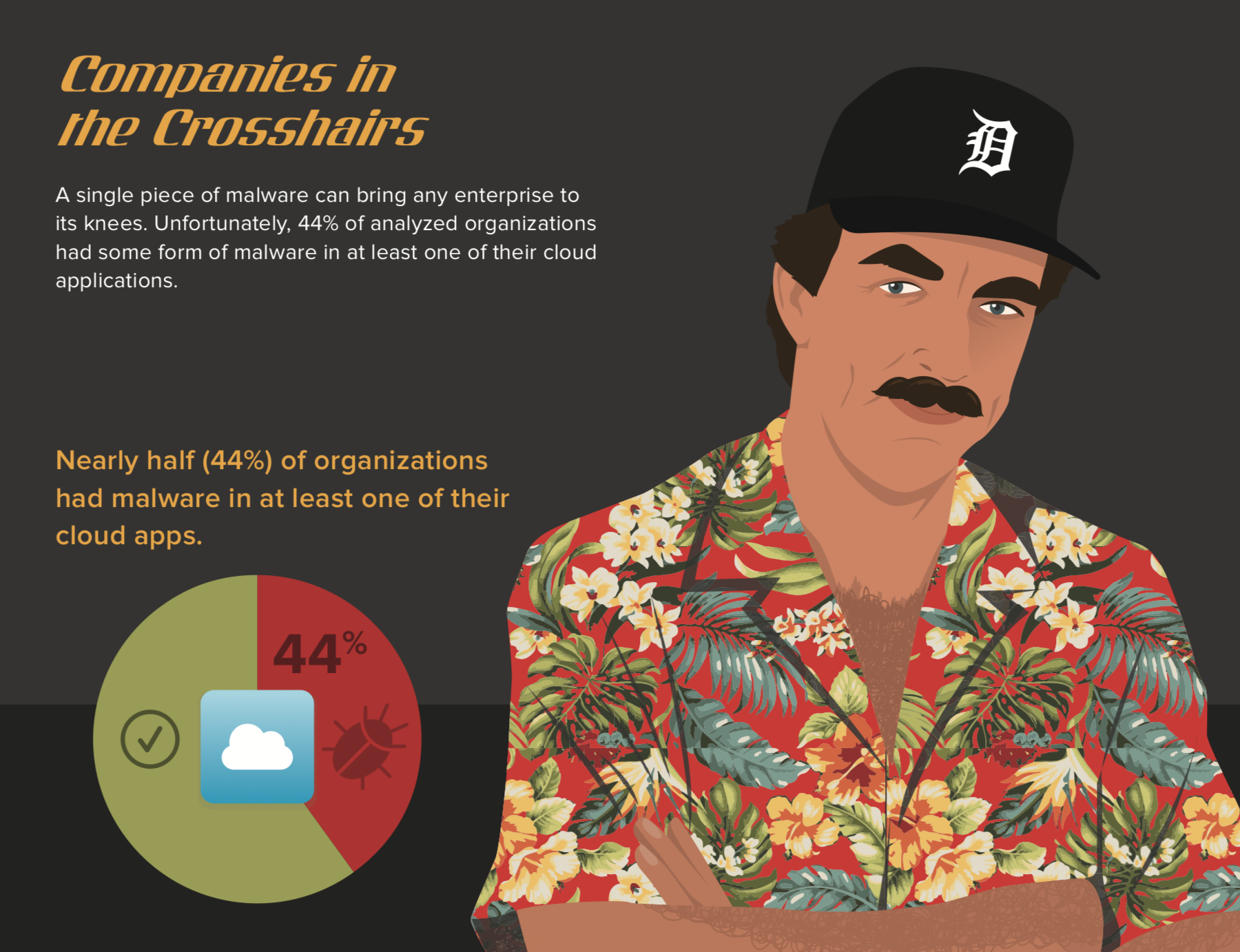
Understanding Cloud Service Data Protection
Cloud service data protection is paramount for businesses leveraging cloud computing. It encompasses policies and practices ensuring the security of data stored and processed in cloud environments. This involves safeguarding data at rest and in transit, guaranteeing integrity, availability, and confidentiality. Robust data protection in the cloud is vital for compliance adherence, safeguarding sensitive data, and preventing unauthorized access and data breaches. Strengthen your defense mechanisms with effective cloud service data protection strategies.

Exploring the Key Elements of Cloud Service Data Protection
Data Encryption: Safeguarding Your Data Assets
Data encryption stands at the forefront of cloud service data protection, serving as a shield against unauthorized access. By encrypting data both at rest and in transit, organizations can bolster the security of their sensitive information. Implementing robust encryption protocols ensures that even if data is intercepted, it remains indecipherable, safeguarding confidentiality effectively.
Access Control: Restricting Unauthorized Data Access
Access control mechanisms are paramount in maintaining the integrity of cloud-stored data. By implementing stringent access control policies, organizations can ensure that only authorized individuals have the privilege to access and modify data within the cloud environment. This crucial element acts as a gatekeeper, preventing unauthorized entities from compromising data security.
Data Backup and Recovery: Ensuring Data Resilience
Data backup and recovery strategies are vital components of cloud service data protection. Regularly backing up data and establishing efficient recovery processes are essential to guaranteeing data availability during unexpected events such as system failures or cyberattacks. Robust backup mechanisms contribute to data resilience, enabling swift recovery and minimal disruptions.
Data Monitoring and Auditing: Strengthening Security Posture
Continuous data monitoring and auditing play a pivotal role in fortifying cloud service data protection. By closely scrutinizing data access and usage patterns, organizations can proactively detect any anomalies or suspicious activities that may indicate potential security breaches. Real-time monitoring enhances incident response capabilities, allowing for prompt actions to mitigate risks effectively.
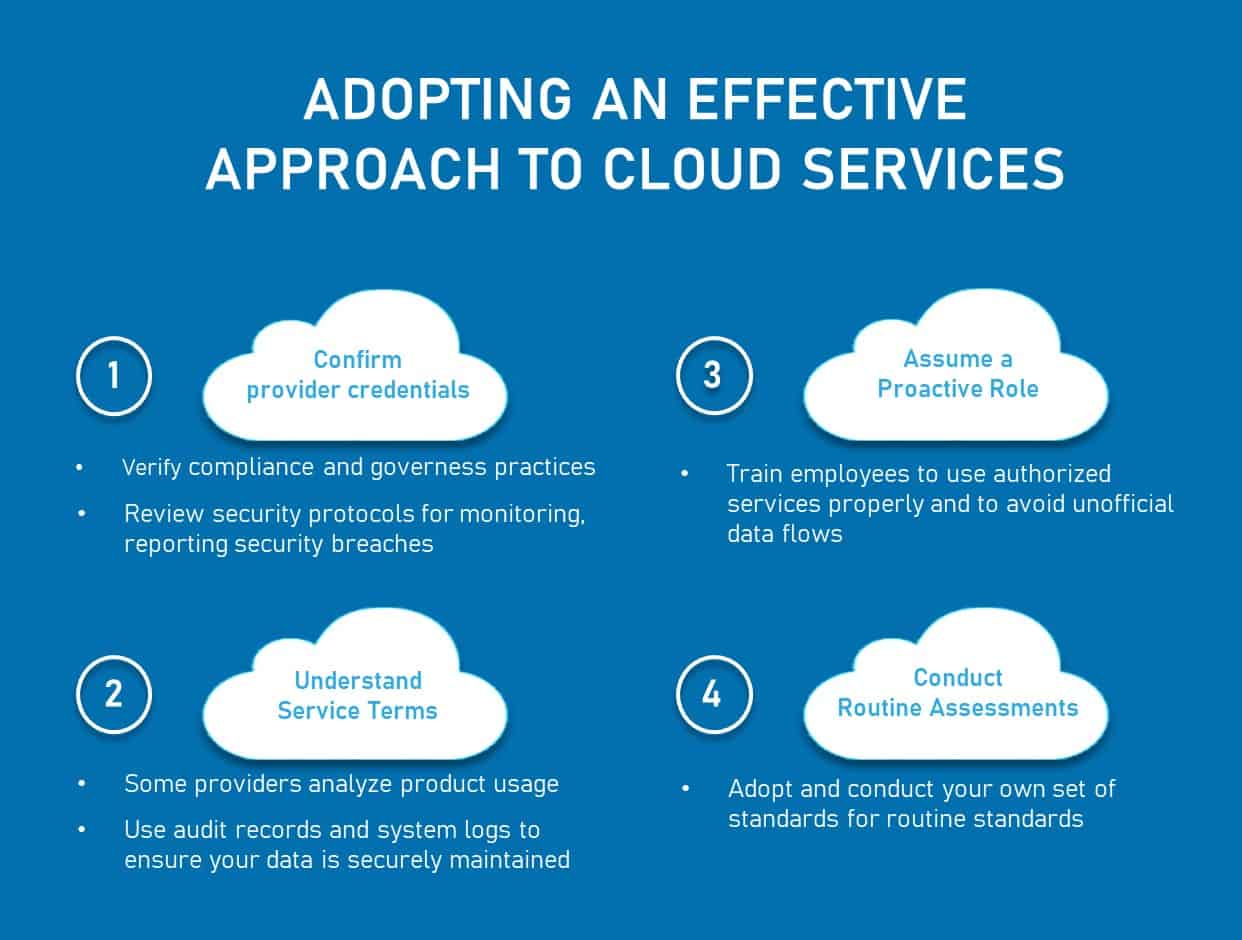
Best Practices for Cloud Service Data Protection
When delving into cloud service data protection, selecting a reputable provider is foundational. Opt for providers with a solid security track record, ensuring compliance with industry standards. Additionally, enforce multi-factor authentication and stringent password policies to fortify access controls and deter unauthorized entry into sensitive data repositories. Regular software updates and security patch installations are imperative to address potential vulnerabilities, enhancing your overall data protection framework. Furthermore, conducting routine security audits and penetration testing aids in identifying and remedying potential security gaps, bolstering your defense mechanisms against cyber threats. By adhering to these best practices, you can proactively safeguard your data assets in cloud environments and maintain a robust defense posture against evolving cyber risks.

Ensuring Compliance with Industry Regulations and Standards
Compliance with regulations like HIPAA, GDPR, and PCI DSS is critical for businesses managing sensitive data in cloud environments. Demonstrating adherence to these standards is vital for cloud service providers to guarantee data protection and evade legal consequences. It is imperative for businesses to grasp their compliance responsibilities and collaborate with providers to fulfill regulatory mandates effectively. Upholding these standards is fundamental in safeguarding data integrity and maintaining trust in cloud service data protection.

Emerging Trends in Cloud Service Data Protection
Cloud-Native Security Tools
Cloud-native security tools are revolutionizing data protection in cloud environments by providing specialized solutions tailored to the unique needs of cloud infrastructure. These tools offer enhanced visibility, control, and protection, empowering organizations to defend against evolving cyber threats effectively. By leveraging cloud-native security tools, businesses can strengthen their defense mechanisms and bolster Cloud service data protection strategies.
Artificial Intelligence (AI) and Machine Learning (ML)
The integration of AI and ML technologies in cloud service data protection enables proactive threat detection and rapid response to security incidents. By analyzing vast amounts of data, AI and ML algorithms can identify patterns, anomalies, and potential risks in real-time, enhancing the overall security posture. Embracing AI and ML empowers organizations to stay one step ahead in safeguarding their sensitive data effectively.
Zero-Trust Security
Zero-trust security is gaining prominence as a fundamental approach to cloud service data protection. By adopting a zero-trust model, organizations verify every access request, regardless of the user’s location or network status. This stringent security paradigm minimizes the risk of unauthorized access and potential data breaches, ensuring a robust and comprehensive defense strategy in cloud computing environments.
Data Sovereignty and Localization
Data sovereignty and localization regulations require organizations to store and process data within specific jurisdictions to comply with data protection laws. Ensuring data residency in designated regions enhances compliance with local regulations and strengthens data governance practices. By adhering to data sovereignty requirements, businesses can maintain legal compliance and reinforce trust in Cloud service data protection measures.

Addressing Challenges in Cloud Service Data Protection
Shared Responsibility Model
The shared responsibility model in cloud service data protection entails a clear delineation of responsibilities between cloud providers and customers. Understanding this model is essential to ensure that security measures are appropriately implemented by both parties, minimizing vulnerabilities and enhancing data protection in cloud environments.
Data Privacy Concerns
Data privacy concerns in cloud service data protection revolve around the ethical and legal obligations associated with collecting, processing, and storing user data. Ensuring compliance with privacy regulations and implementing robust data protection measures are crucial to building trust with users and maintaining the confidentiality of sensitive information.
Vendor Lock-In
Vendor lock-in poses a significant challenge in cloud service data protection, as organizations risk becoming overly reliant on a single cloud provider. To mitigate this risk, businesses should adopt a multi-cloud strategy, enabling data portability and reducing dependence on any single vendor, thus enhancing flexibility and security.
Managing Data Across Multiple Cloud Platforms
Managing data across multiple cloud platforms introduces complexities in ensuring consistent data protection practices. Organizations must establish unified security policies, implement encryption mechanisms, and monitor data access diligently to safeguard information in hybrid or multi-cloud environments effectively. Adopting a comprehensive approach to data management is key to mitigating risks and maintaining data integrity.
