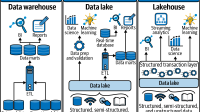
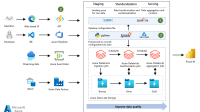
Discover the importance of cloud audit trails in enhancing security, compliance, and accountability within organizations. By implementing robust audit trails, businesses can effectively track and monitor user activities, system changes, and data access, ultimately reducing the risk of data breaches. Learn how cloud audit trails play a crucial role in promoting transparency and strengthening cybersecurity measures to safeguard sensitive information and maintain regulatory compliance.
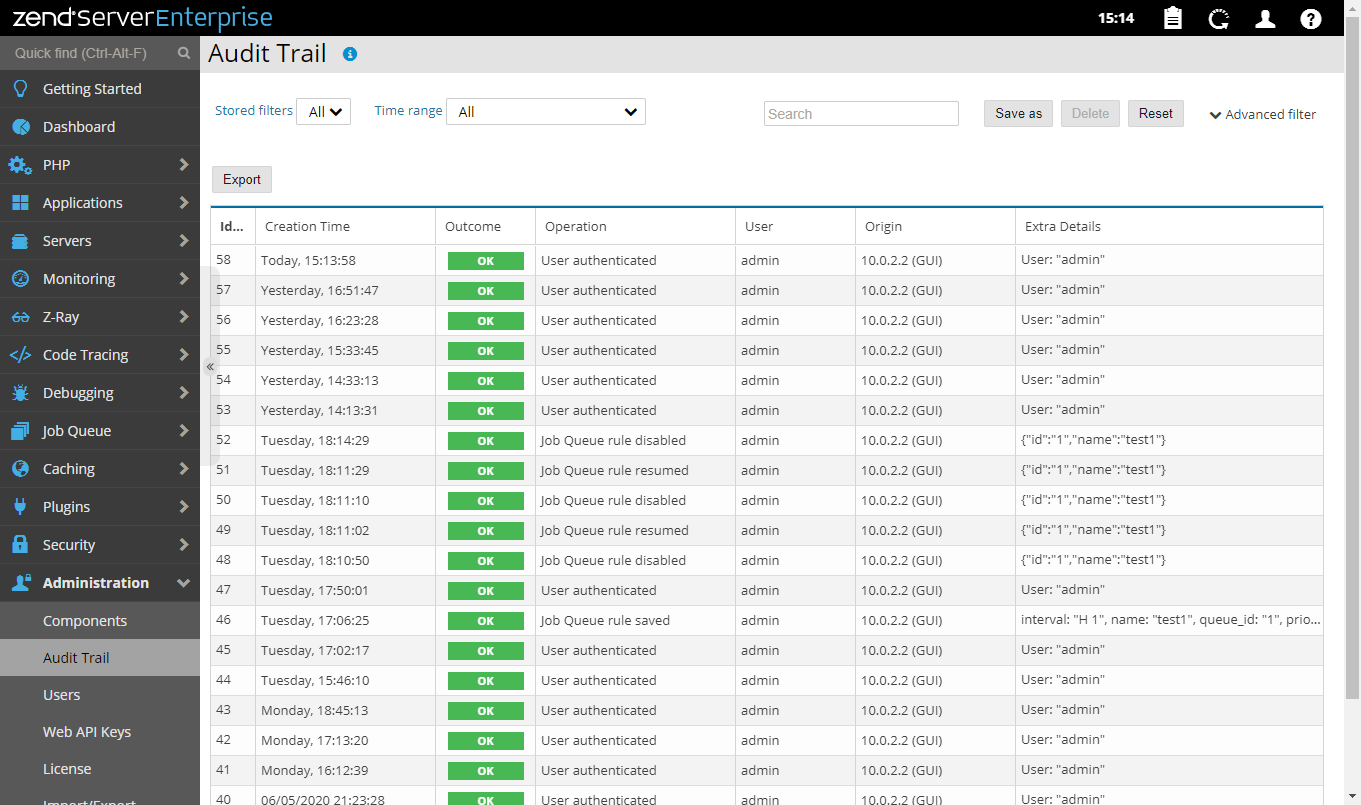
Advantages of Cloud Audit Trails
Enhanced Security and Compliance
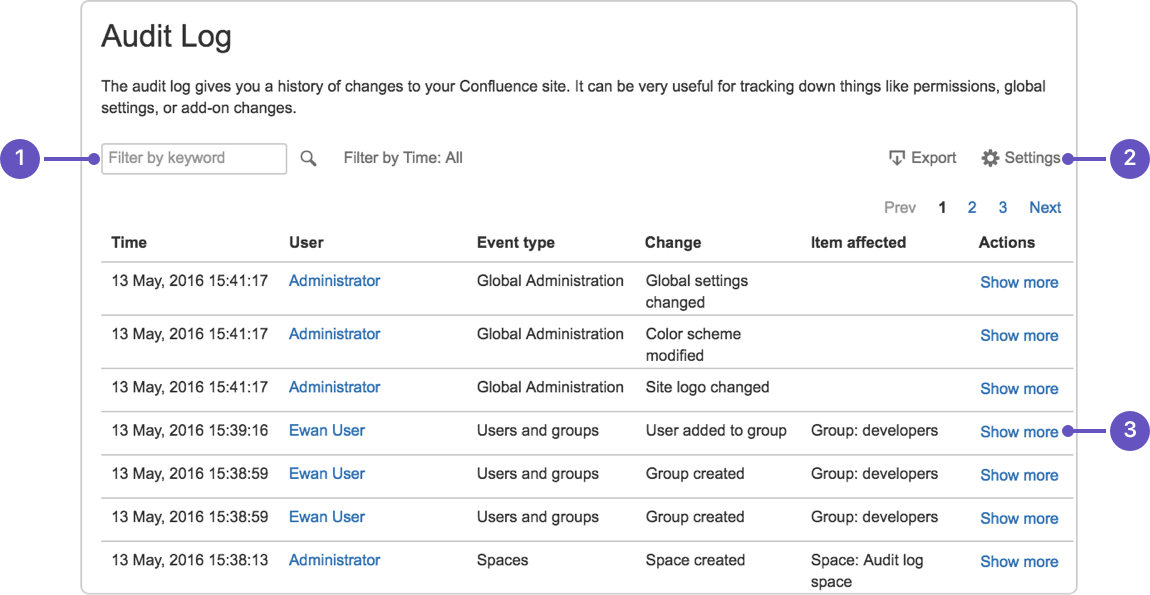
Cloud audit trails offer a detailed account of user actions, aiding organizations in adhering to regulatory standards. By providing comprehensive logs of activities, they ensure compliance requirements are met, enhancing overall data security.
Improved Threat Detection and Response
By enabling swift identification and investigation of anomalous behaviors, cloud audit trails empower security teams to promptly respond to potential threats. This proactive approach enhances the organization’s ability to detect and mitigate security incidents effectively.
Reduced Risk of Data Breaches
Cloud audit trails assist in pinpointing vulnerabilities within the system, allowing proactive intervention to mitigate risks and prevent data breaches. This proactive stance significantly reduces the likelihood of unauthorized access and data loss incidents.
Increased Accountability and Transparency
With a clear trail of user actions, cloud audit trails foster accountability by detailing the who, what, when, and where of each activity. This transparency not only deters internal misconduct but also helps in swiftly attributing any unauthorized actions, enhancing governance and trust within the organization.
Exploring Types of Cloud Audit Trails
1. System Logs:
System logs play a critical role in capturing events like system configuration changes and security alerts within the cloud platform. These logs provide valuable insights into the health and security of the system, enabling proactive monitoring and rapid responses to potential threats.
2. User Logs:
User logs are essential for recording user activities such as logins, data access, and file modifications. By tracking user actions, organizations can maintain accountability, detect unauthorized access, and ensure compliance with security protocols and data governance regulations.
3. Application Logs:
Monitoring application logs in the cloud offers visibility into application-specific events, usage patterns, and performance metrics. These logs help in troubleshooting application issues, optimizing performance, and ensuring the reliability of cloud-based applications for seamless user experiences.
4. API Logs:
API logs are crucial for tracking calls made to cloud APIs, revealing how applications interact with cloud services and resources. Analyzing API logs allows organizations to identify inefficiencies, monitor integrations, and enhance overall system performance by understanding the usage and behavior of applications within the cloud environment.
Incorporating diverse types of cloud audit trails, including system, user, application, and API logs, provides organizations with a comprehensive view of their cloud environments, enabling enhanced security, improved operational efficiency, and better compliance management. By leveraging these audit trail types, businesses can strengthen their cybersecurity posture and mitigate risks effectively.

Best Practices for Implementing Cloud Audit Trails
Define Clear Logging Policies
Establishing precise logging policies is paramount in reaping the full benefits of cloud audit trails. Clearly outline the events and activities that necessitate logging, including user actions, system modifications, and data access. Define retention periods to ensure compliance with regulations and internal security standards.
Use a Centralized Logging Solution
Implementing a centralized logging solution streamlines the management and analysis of audit trails. By consolidating logs from various sources into a single repository, organizations can simplify auditing processes, enhance visibility, and facilitate prompt incident response. Centralization aids in streamlining investigations and ensuring comprehensive oversight.
Configure Alerts and Notifications
Enabling alerts and notifications is a proactive measure to bolster security vigilance. By configuring real-time alerts, administrators can promptly address potential threats and suspicious activities, mitigating risks effectively. Setting up automated notifications empowers organizations to respond swiftly to security incidents and deviations from established norms.
Regularly Review and Analyze Logs
Continuous monitoring and analysis of audit logs are indispensable practices in maintaining a robust security posture. By routinely reviewing logs, organizations can uncover patterns, detect irregularities, and preempt security breaches. Analyzing logs not only fortifies defenses but also aids in refining security measures based on historical data insights.
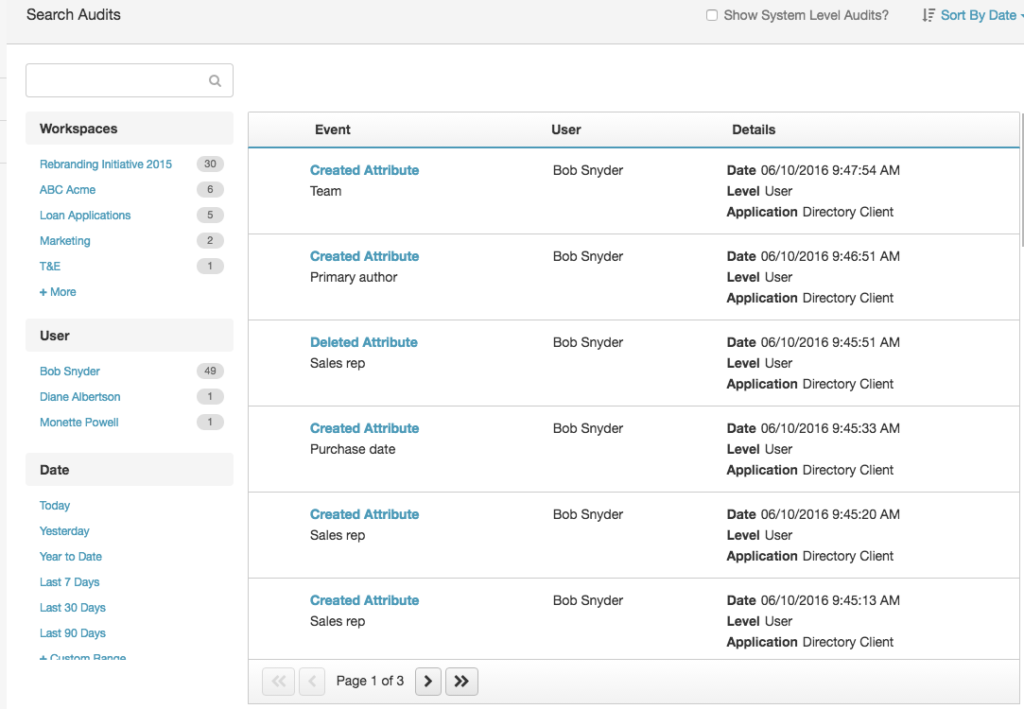
Addressing the Challenges of Cloud Audit Trails
Managing Volume and Complexity
One of the primary challenges of cloud audit trails lies in the sheer volume and complexity of logs generated. Dealing with massive amounts of data poses difficulties in effectively managing and analyzing the information to derive meaningful insights, making it essential to have efficient log management tools and processes in place.
Ensuring Data Privacy
Data privacy concerns are paramount in the context of audit trails as they often contain sensitive information. Safeguarding this data against unauthorized access and breaches is crucial. Implementing robust encryption methods and access controls is necessary to protect the integrity and confidentiality of the audit trail information.
Cost Implications
The cost considerations associated with cloud audit trails revolve around the expenses incurred in logging, storing, and analyzing extensive data sets. Especially in large-scale cloud deployments, these costs can escalate rapidly. Organizations need to strike a balance between data retention policies and cost-effectiveness to manage their audit trail expenses efficiently.
Integration Complexity
Integrating cloud audit trails with existing security and compliance systems can pose a significant challenge. Ensuring seamless integration requires time, resources, and expertise to align the audit trail mechanisms with established systems effectively. Overcoming compatibility issues and ensuring data consistency across platforms are key considerations for successful integration efforts.
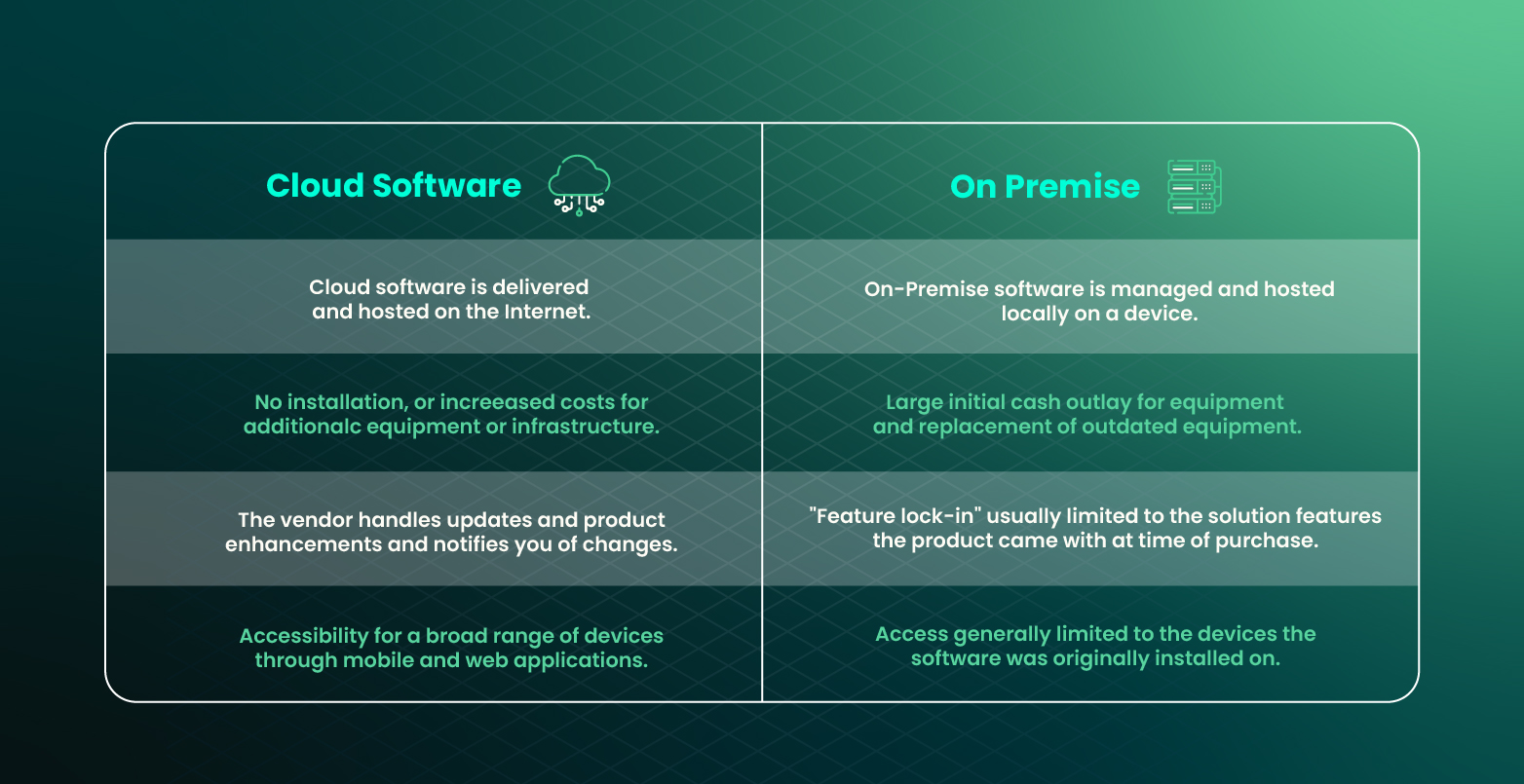
Cloud Audit Trails vs. Traditional On-Premises Logs
Centralized vs. Distributed
Cloud audit trails offer a centralized approach, aggregating all activity logs into a single platform. This centralized view provides a comprehensive oversight of cloud activities, enhancing security monitoring and incident response capabilities. In contrast, traditional on-premises logs are often distributed across different systems, making it challenging to consolidate and analyze data effectively.
Scalability
One of the key advantages of cloud audit trails is their scalability. With cloud-based solutions, organizations can effortlessly scale their logging capabilities to accommodate large volumes of data generated by diverse cloud services and applications. This scalability ensures that no critical event goes unnoticed due to log storage limitations, a common constraint in traditional on-premises logging setups.
Accessibility
Cloud audit trails excel in accessibility by allowing administrators to monitor and review logs remotely. This remote access feature empowers IT teams to investigate incidents promptly, no matter their location, ensuring real-time visibility into system activities. In contrast, traditional on-premises logs often require physical access to servers or intricate VPN setups for remote log analysis, hindering operational efficiency.
Cost-Effectiveness
Cloud audit trails present a cost-effective alternative to traditional on-premises logging mechanisms, particularly for large enterprises. By leveraging cloud infrastructure, organizations can avoid significant upfront investments in on-premises hardware and maintenance costs. The pay-as-you-go model of cloud audit trails also enables businesses to align logging expenses with actual usage, optimizing cost efficiency without compromising security and compliance measures.
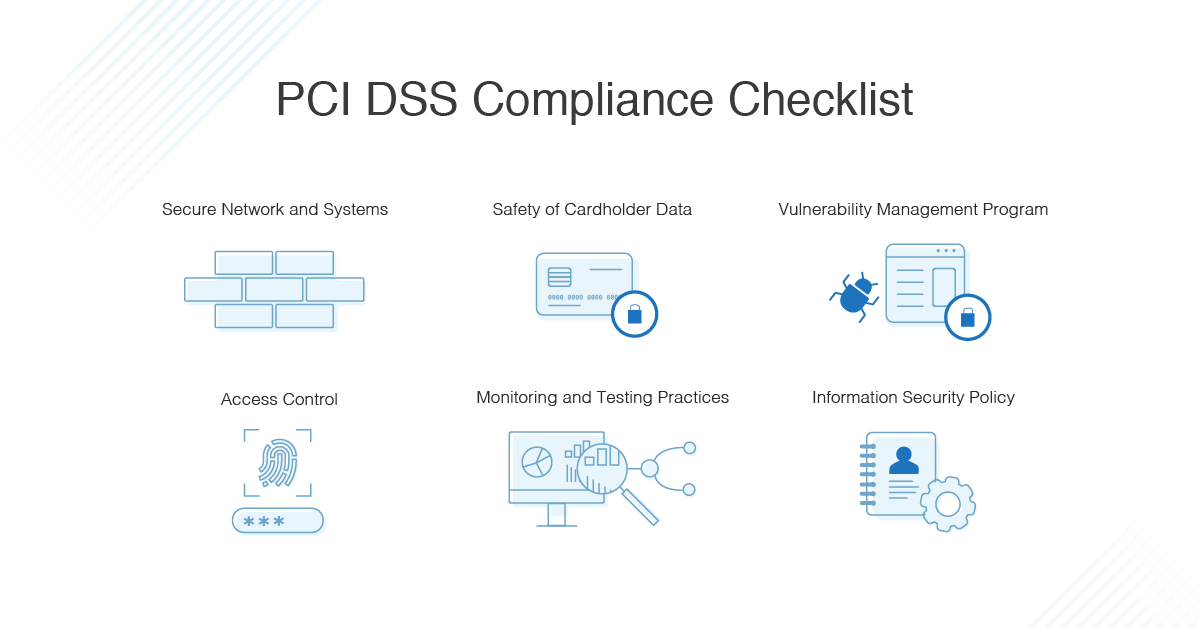
Compliance and Regulatory Considerations
Ensuring Compliance with Cloud Audit Trails
Cloud audit trails are essential for organizations to meet various compliance standards, such as GDPR, HIPAA, PCI DSS, and ISO 27001. These regulations mandate stringent data protection measures, and cloud audit trails play a pivotal role in demonstrating adherence to these requirements.
GDPR Compliance and Cloud Audit Trails
Implementing cloud audit trails is crucial for GDPR compliance. By tracking and recording user activities and data access, organizations can ensure transparency and accountability, aligning with GDPR’s emphasis on data protection and privacy rights.
HIPAA Regulations and Audit Trails in Healthcare
For healthcare organizations, maintaining compliance with HIPAA is non-negotiable. Cloud audit trails provide evidence of data security measures, ensuring the protection of sensitive patient information and meeting HIPAA’s strict regulatory standards.
PCI DSS Requirements and Cloud Audit Trails
Businesses that handle payment card data must adhere to PCI DSS standards to prevent financial fraud. Cloud audit trails assist in monitoring and securing cardholder data transactions, making it easier to comply with PCI DSS requirements and safeguard sensitive financial information.
ISO 27001 and Cloud Audit Trails
ISO 27001 sets the benchmark for information security management systems. Cloud audit trails enable organizations to track security incidents, monitor system changes, and demonstrate compliance with ISO 27001 standards, ensuring robust data protection practices are in place.
Emerging Trends in Cloud Audit Trails
AI and ML Advancements in Log Analysis
The integration of Artificial Intelligence (AI) and Machine Learning (ML) algorithms is revolutionizing log analysis in cloud audit trails. By leveraging AI and ML capabilities, organizations can streamline the process, identify patterns, and proactively detect anomalies, enhancing the efficiency and effectiveness of auditing activities.
Real-Time Monitoring and Alerting Evolution
The shift towards real-time monitoring and alerting functionalities in cloud audit trails is a significant trend. This evolution enables organizations to promptly detect suspicious activities, potential threats, and security breaches, ensuring a swift response to mitigate risks and safeguard critical data in dynamic cloud environments.
Integration with SOAR Platforms for Automation
Cloud audit trails are increasingly being integrated with Security Orchestration, Automation, and Response (SOAR) platforms. This fusion allows for automated incident response, enabling seamless coordination between audit findings and security actions, improving response times, and reducing manual intervention for enhanced cybersecurity posture.
Leveraging Blockchain for Immutable Logging
The adoption of blockchain technology for creating tamper-proof audit trails is gaining traction. By utilizing blockchain’s inherent properties of decentralization and cryptographic hashing, organizations can establish immutable logs that maintain the integrity and authenticity of audit trails, providing a robust defense against unauthorized alterations or deletions.