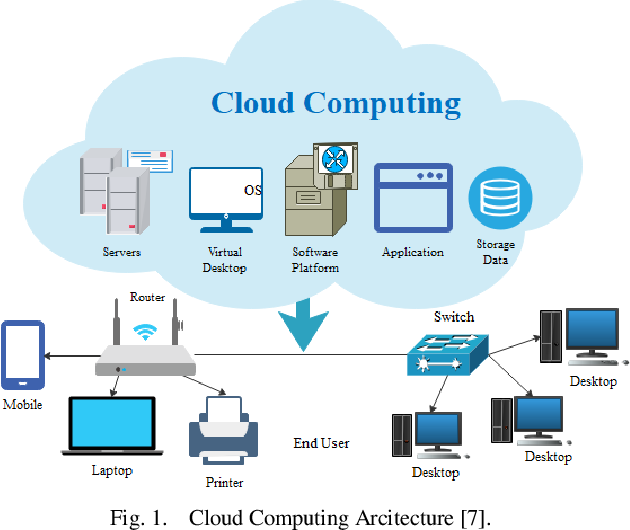
With the ever-increasing reliance on cloud computing, the safety of your servers has develop into paramount. Whether or not you’re a small enterprise proprietor or a big enterprise, your knowledge is susceptible to being compromised if correct safety measures should not in place. On this weblog article, we are going to delve into the intricacies of cloud server safety, offering you with a complete understanding of the steps you might want to take to safeguard your priceless info.
At first, it’s essential to grasp the potential threats that cloud servers face. From exterior assaults by hackers to inside breaches brought on by unauthorized entry, the dangers are numerous and ever-evolving. To fight these threats, organizations should implement sturdy safety measures that embody each preventive and proactive methods. Allow us to now discover the important thing points of cloud server safety intimately.
1. The Significance of Robust Authentication Mechanisms
Guaranteeing that solely licensed people have entry to your cloud servers is the primary line of protection towards potential breaches. This part will talk about the importance of multifactor authentication, biometrics, and different authentication mechanisms, together with greatest practices for his or her implementation.
2. Encryption: Defending Your Information from Prying Eyes
Encryption performs a significant position in safeguarding your knowledge from unauthorized entry throughout storage and transmission. This part will delve into totally different encryption strategies, similar to symmetric and uneven encryption, and make clear how encryption keys are managed.
3. Securing Cloud Infrastructure: A Basis for Sturdy Safety
With out a safe infrastructure, even essentially the most superior safety measures may be rendered ineffective. On this part, we are going to discover the important components of a safe cloud infrastructure, together with community safety, bodily safety, and catastrophe restoration plans.
4. Patch Administration: Staying Forward of Vulnerabilities
Software program vulnerabilities may be exploited by attackers to realize unauthorized entry to your servers. This part will delve into the significance of patch administration and description efficient methods for well timed updates and vulnerability remediation.
5. Intrusion Detection and Prevention Programs: Detecting and Mitigating Assaults
By constantly monitoring community visitors and analyzing patterns, intrusion detection and prevention programs play an important position in figuring out and mitigating potential assaults. This part will talk about the significance of those programs and the assorted methods they make use of to safeguard cloud servers.
6. Information Backups: Getting ready for the Worst-Case State of affairs
Information loss can happen attributable to varied causes, together with {hardware} failures, pure disasters, or human errors. This part will spotlight the importance of standard knowledge backups and description greatest practices for creating redundant copies of your crucial info.
7. Worker Schooling and Consciousness: The Human Ingredient
Even with essentially the most superior safety measures in place, human error can nonetheless pose a big threat to cloud server safety. This part will emphasize the significance of training workers about safety greatest practices and fostering a tradition of consciousness inside the group.
8. Steady Monitoring and Auditing: Guaranteeing Ongoing Safety
Cloud server safety will not be a one-time activity; it requires steady monitoring and auditing to establish potential vulnerabilities and monitor any suspicious actions. This part will discover the importance of real-time monitoring instruments and common safety audits.
9. Compliance: Assembly Regulatory Necessities
Relying in your business, it’s possible you’ll be topic to particular regulatory necessities regarding knowledge safety. This part will present an outline of widespread compliance requirements and talk about methods for making certain that your cloud servers meet the required standards.
10. Incident Response and Restoration: Minimizing the Influence of Breaches
Regardless of all preventive measures, breaches can nonetheless happen. This part will give attention to incident response and restoration methods, guiding you on the best way to successfully reply to safety incidents, reduce harm, and restore regular operations.
In conclusion, cloud server safety is a multifaceted endeavor that requires a complete understanding of potential threats and the implementation of applicable measures. By adopting sturdy authentication mechanisms, encryption, safe infrastructure, and proactive monitoring, organizations can considerably improve the safety of their priceless knowledge. Keep in mind, cloud server safety is an ongoing course of, and staying up-to-date with the most recent safety practices is crucial on this ever-evolving digital panorama.