Are you looking to enhance your organization’s security measures with cloud identity management solutions? In this comprehensive guide, we will delve into the world of Cloud identity management, exploring its benefits, key features, implementation strategies, and best practices. Whether you are a seasoned IT professional or just starting out, understanding how to navigate the complexities of Cloud identity management is crucial in today’s digital landscape. Discover how to choose the right provider and stay ahead of future trends in this ever-evolving field.

Deep Dive into Cloud Identity Management Solutions
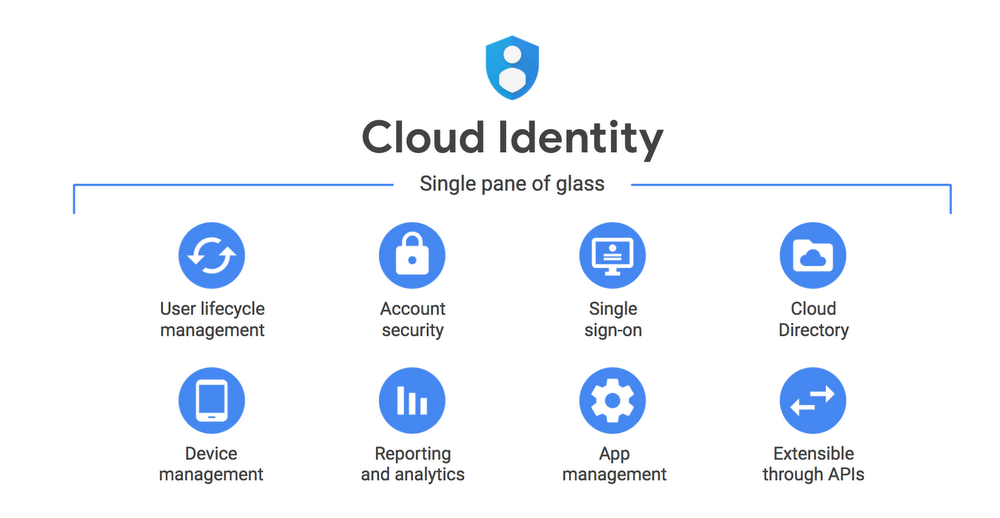
Cloud Identity Management (CIM) revolutionizes user identity governance in the digital era. It centralizes user identity, access, and security management across diverse cloud platforms. CIM ensures a robust security framework by consolidating user accounts, roles, and permissions under one roof, enhancing administrative efficiency while fortifying data protection. By enforcing uniform identity policies, CIM diminishes vulnerabilities and enhances operational fluidity across cloud services. Streamlining user lifecycle processes, CIM optimizes organizational efficiency and data security.
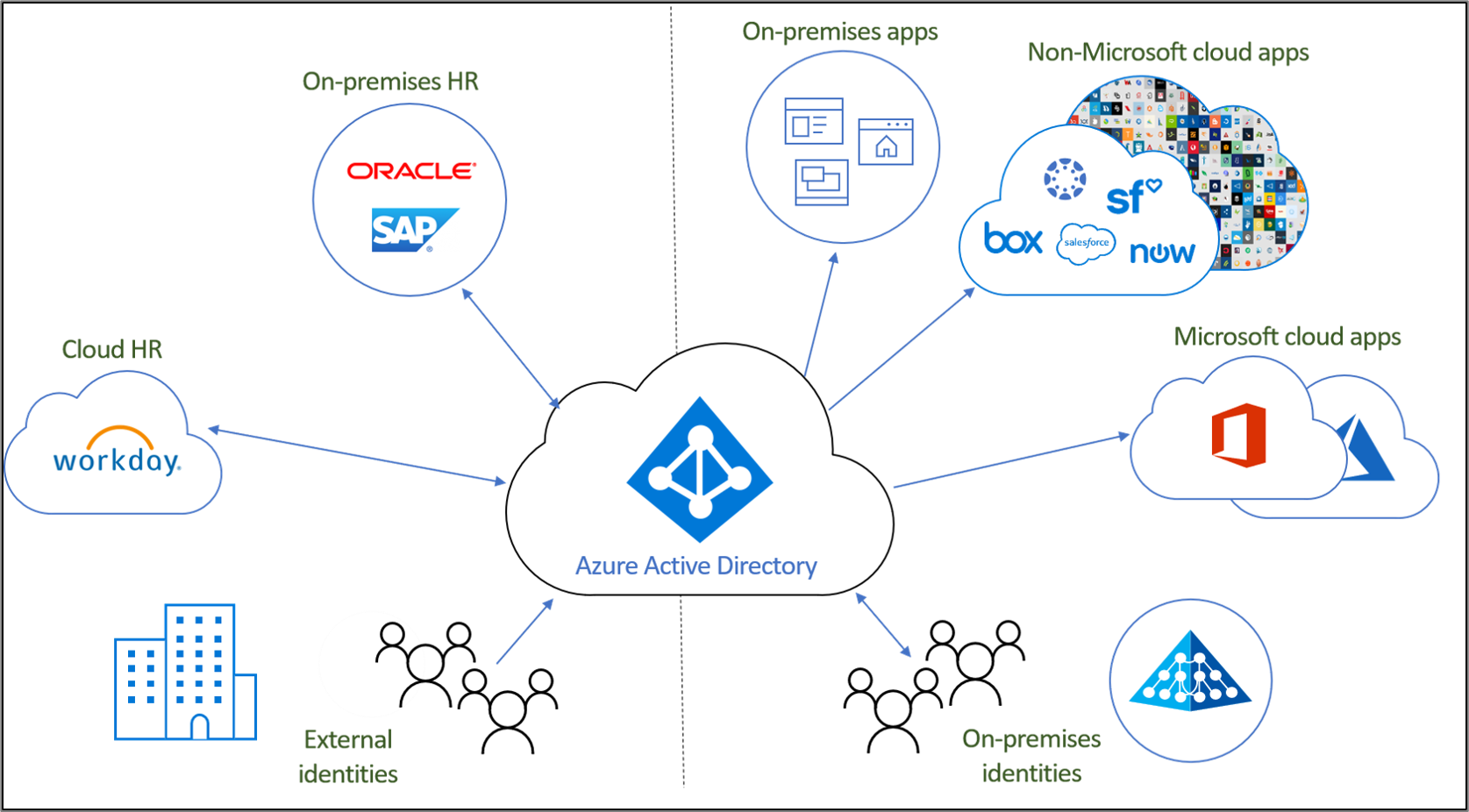
Benefits of Cloud Identity Management
Strengthened Security
Cloud Identity Management solutions significantly enhance security measures by centralizing identity management processes. By incorporating least-privilege access principles, organizations can ensure that users only have access to the resources necessary for their roles, reducing the risk of unauthorized data breaches and enhancing overall data security.
Elevated User Experience
The implementation of Single Sign-On (SSO) and Multi-Factor Authentication (MFA) in Cloud Identity Management solutions offers users a streamlined and secure authentication process. This seamless login experience not only boosts user productivity but also fortifies the organization’s defense against unauthorized access attempts, hence safeguarding sensitive data effectively.
Streamlined Administrative Tasks
Cloud Identity Management solutions streamline administrative tasks through automated user provisioning, deprovisioning, and lifecycle management functionalities. By automating these processes, IT departments can significantly reduce manual interventions, thereby cutting down on operational costs and improving overall efficiency within the organization.
Regulatory Compliance Assistance
Cloud Identity Management solutions play a pivotal role in aiding organizations to comply with stringent regulatory requirements. By providing centralized audit trails and robust reporting mechanisms, CIM ensures that organizations can easily track and monitor user activities, thus facilitating compliance with industry regulations and standards.

Exploring the Key Features of Cloud Identity Management Solutions
Centralized Identity Repository
One of the fundamental pillars of Cloud Identity Management solutions is the centralized identity repository. This feature acts as a secure vault, storing and managing user identities, attributes, and access rights in a centralized location. By having a consolidated database, organizations can efficiently control user access across various systems and applications, enhancing security and streamlining user management processes.
Single Sign-On (SSO) Capability
Cloud Identity Management solutions offer the convenience of Single Sign-On (SSO), enabling users to access multiple applications and platforms using a single set of credentials. This feature not only simplifies the user experience but also boosts productivity by eliminating the need to remember and enter multiple passwords. With SSO, organizations can enhance security while ensuring seamless access to resources.
Multi-Factor Authentication (MFA) Integration
To bolster security measures, Cloud Identity Management solutions incorporate Multi-Factor Authentication (MFA) functionality. MFA adds an extra layer of protection by requiring users to provide multiple forms of verification before accessing sensitive data or applications. By combining something a user knows (password) with something they have (token or biometric data), MFA significantly reduces the risk of unauthorized access.
Role-Based Access Control (RBAC) Implementation
Cloud Identity Management solutions empower organizations with Role-Based Access Control (RBAC) capabilities, allowing administrators to define and enforce user permissions based on specific roles and responsibilities within the organization. By assigning roles with corresponding access levels, RBAC ensures that users only have the necessary privileges to perform their job functions, minimizing the risk of unauthorized data breaches and ensuring compliance with security policies.

Choosing the Right Cloud Identity Management Provider
Tailoring Your Choice to Your Organization’s Needs
When selecting a Cloud Identity Management solutions provider, it’s crucial to align their offerings with your organization’s unique characteristics. Consider factors like company size, industry regulations, and specific security demands to ensure the chosen provider meets your bespoke requirements effectively.
Assessing Scalability, Reliability, and Support
Evaluate the provider’s scalability to accommodate your organization’s growth, reliability in ensuring system uptime, and support capabilities for seamless integration and continuous assistance. A robust provider should offer scalable solutions, reliable services, and responsive support to guarantee optimal performance.
Seamless Integration and Application Compatibility
Look for Cloud Identity Management solutions that seamlessly integrate with your current IT infrastructure and applications. Compatibility is vital to streamline operations, enhance user experience, and maximize the benefits of the solution. Ensure that the chosen provider supports the integration of your existing systems effortlessly.
Cost-Effective Solutions for Budget Alignment
Compare pricing models offered by different providers to find a solution that meets your budget constraints without compromising on quality. Choosing a cost-effective Cloud Identity Management provider ensures that you can leverage advanced security features and services within a budget that aligns with your organization’s financial goals.

Implementing Cloud Identity Management: A Strategic Approach
When implementing Cloud Identity Management solutions, meticulous planning and design are paramount. Tailor the implementation to meet your organization’s specific requirements, ensuring seamless integration and optimal functionality. Prioritize assessing current user identities and access rights to facilitate a smooth migration to the cloud directory, streamlining processes and enhancing security.
Enhance your organization’s security posture by configuring Single Sign-On (SSO) and Multi-Factor Authentication (MFA) within your Cloud Identity Management system. This dual approach not only fortifies data protection but also simplifies user experience by providing secure access across multiple platforms with ease.
Regular monitoring and auditing of your Cloud Identity Management solution are essential practices to uphold its efficacy. By conducting routine checks and assessments, you can proactively identify and address any potential vulnerabilities or irregularities, ensuring the ongoing security and efficiency of your CIM system. Stay vigilant in safeguarding your organization’s digital assets through continuous oversight and optimization efforts.
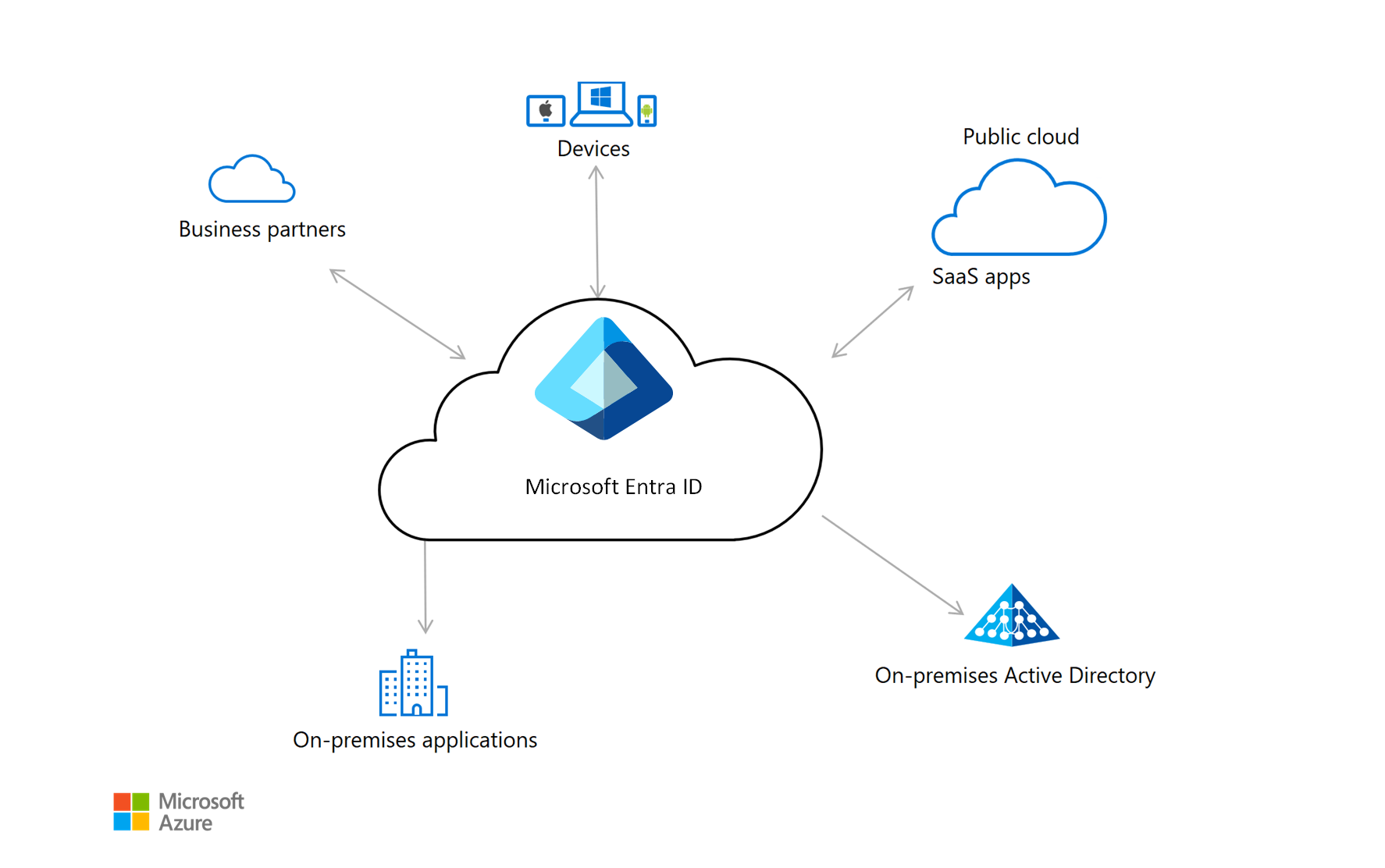
Emerging Trends in Cloud Identity Management
Increased Adoption of Identity as a Service (IDaaS)
As organizations move towards streamlined cloud solutions, the adoption of Identity as a Service (IDaaS) is on the rise. IDaaS offers centralized identity and access management, simplifying user authentication across various applications and devices, enhancing security, and optimizing user experience within Cloud Identity Management solutions.
Integration of AI and ML for Enhanced Security
The integration of Artificial Intelligence (AI) and Machine Learning (ML) in Cloud Identity Management solutions is revolutionizing security protocols. These technologies bolster threat detection, automate responses to potential risks, and continuously learn from patterns to fortify protection layers, ensuring proactive security measures in an ever-evolving digital landscape.
Biometric Authentication and Zero Trust Models
Biometric authentication methods like fingerprint scanning, facial recognition, and iris scans are gaining momentum in ensuring robust identity verification. Zero trust security models, which validate each access request regardless of location, strengthen security postures, making unauthorized access exceedingly challenging, thereby safeguarding sensitive information effectively.
Essential Component of Digital Transformation
Cloud identity management is no longer an option but a necessity for organizations undergoing digital transformation. Seamless integration of Cloud Identity Management solutions into core business processes not only enhances security but also fosters agility, scalability, and innovation, enabling organizations to adapt to dynamic market trends and stay competitive in the digital era.