Learn all about cloud vulnerability management in this ultimate guide. Explore the key principles, benefits, challenges, best practices, and emerging trends in the ever-evolving landscape of cloud security. Discover how organizations can effectively protect their cloud environments against cyber threats and ensure data integrity. Dive into the world of cloud vulnerability management to enhance your understanding and readiness in securing your digital assets.

Delving into the Depths of Cloud Vulnerability Management
Understanding the Essence of Cloud Vulnerability Management
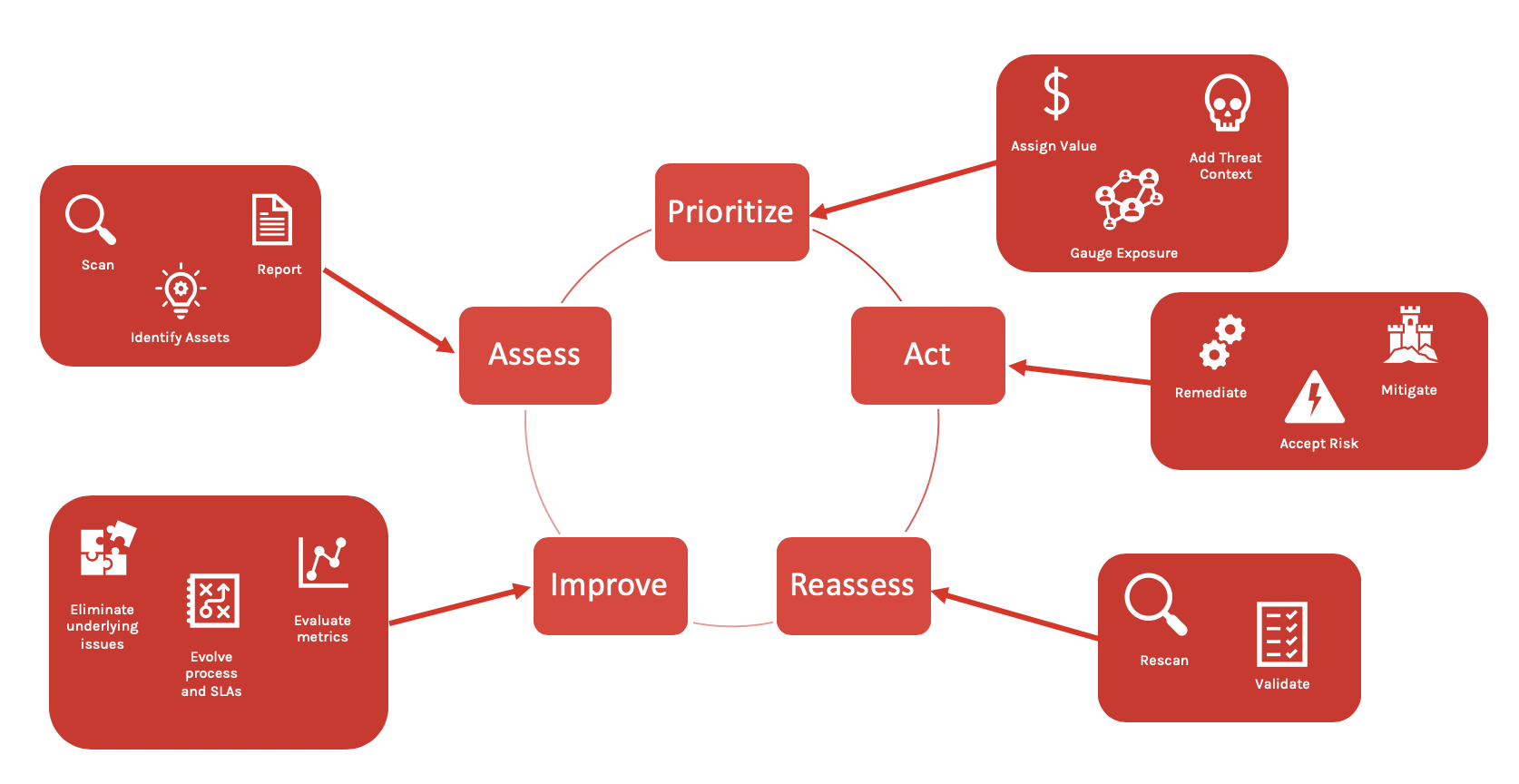
Cloud Vulnerability Management signifies the proactive process of recognizing, evaluating, and minimizing vulnerabilities that may compromise cloud systems. It is a pivotal component in fortifying organizations against potential cyber threats by safeguarding cloud infrastructure, applications, and sensitive data. This multifaceted task necessitates a holistic strategy integrating diverse security mechanisms, protocols, and industry-standard methodologies.
Safeguarding Cloud Assets with Vigilance
By instituting robust Cloud Vulnerability Management protocols, businesses can shield their cloud assets from malicious activities, breaches, and vulnerabilities. This approach ensures the resilience of cloud infrastructure, shielding critical applications and data from exploitation. Moreover, a meticulous vulnerability management framework enables organizations to uphold data integrity, maintain operational continuity, and preserve customer trust in their cloud services.

Exploring the Key Principles of Cloud Vulnerability Management
Proactive Identification and Assessment of Vulnerabilities
Effective Cloud Vulnerability Management entails the proactive identification and assessment of vulnerabilities across cloud environments. By utilizing robust scanning tools and methodologies, organizations can detect potential weaknesses before they are exploited by cyber threats, bolstering preemptive security measures to safeguard critical data and systems.
Prioritization of Vulnerabilities Based on Risk and Impact
Prioritizing vulnerabilities according to their risk levels and potential impact on the organization is a fundamental principle in Cloud Vulnerability Management. This strategic approach enables security teams to allocate resources efficiently, focusing on addressing high-risk vulnerabilities that pose significant threats to the integrity of cloud infrastructures and sensitive information.
Timely Remediation and Patching of Vulnerabilities
Timely remediation and patching play a pivotal role in Cloud Vulnerability Management. Swiftly addressing identified vulnerabilities through remediation and patching procedures helps prevent potential security breaches and data compromises. Establishing a structured process for remediation ensures that vulnerable areas are promptly secured, minimizing the window of opportunity for cyber attackers.
Continuous Monitoring and Scanning for New Vulnerabilities
Continuous monitoring and scanning for new vulnerabilities are essential practices in Cloud Vulnerability Management. By staying vigilant and employing automated monitoring tools, organizations can actively track and assess emerging threats to their cloud environments. This real-time approach allows for timely identification and mitigation of vulnerabilities, bolstering overall security posture.
By adhering to these key principles, organizations can enhance their Cloud Vulnerability Management strategies, fortifying their defenses against evolving cyber threats and ensuring the resilience of their cloud infrastructure.

Challenges in Cloud Vulnerability Management
The Complexity and Scale of Cloud Environments
Managing vulnerabilities across diverse cloud infrastructures can be daunting due to the complex nature of modern cloud setups. The vast scale of cloud environments amplifies the challenge, requiring robust strategies to identify and remediate vulnerabilities effectively.
The Rapidly Evolving Threat Landscape
Cloud environments face a continuously evolving threat landscape with sophisticated and diverse cyber threats. Staying ahead of these threats demands constant monitoring, proactive vulnerability assessment, and agile response mechanisms to mitigate the risks effectively.
Lack of Visibility and Control Over Third-Party Cloud Services
Organizations often struggle with the lack of visibility and control when it comes to third-party cloud services. Integrating these services into vulnerability management processes poses challenges in maintaining a thorough understanding and oversight of potential security gaps.
Skills and Resource Constraints
Skill shortages and resource constraints are common challenges faced in cloud vulnerability management. Building and retaining a skilled cybersecurity team, allocating adequate resources, and staying updated with the latest tools and techniques can be demanding tasks for organizations.
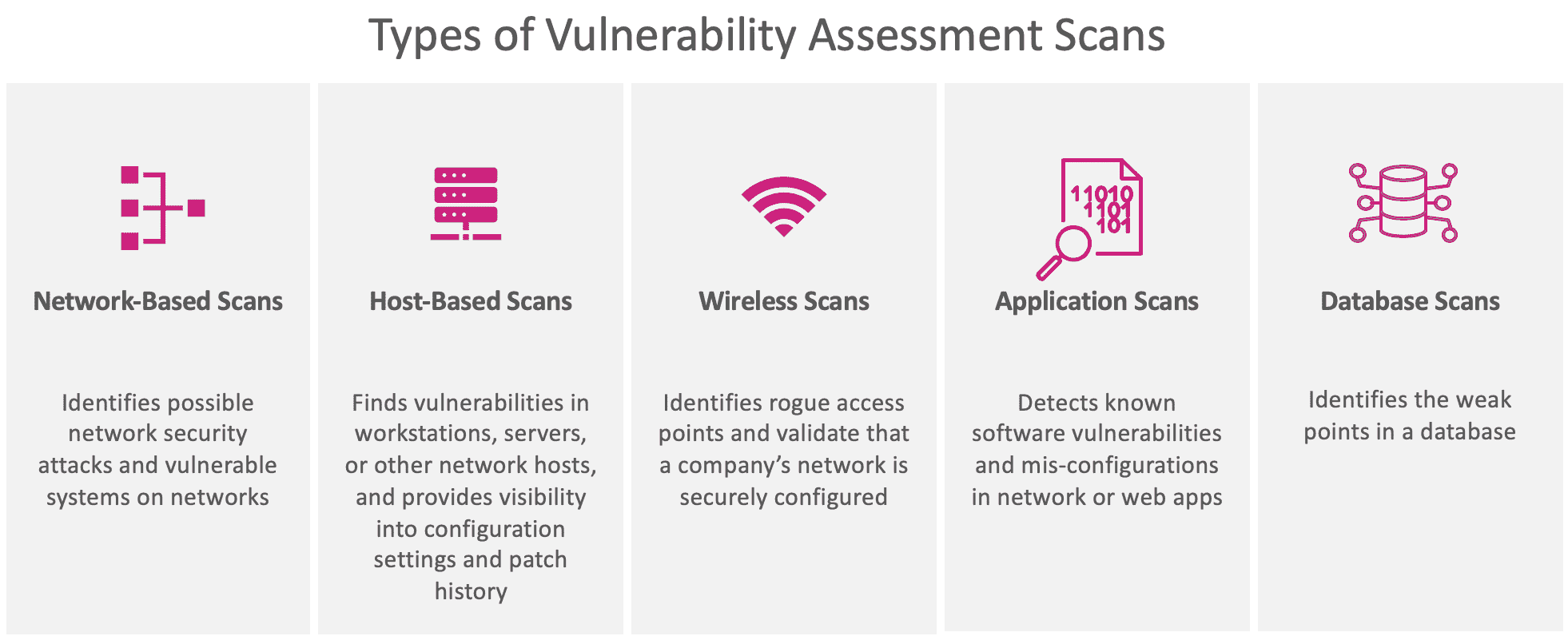
Best Practices for Cloud Vulnerability Management
Implement Automated Vulnerability Scanning Tools
Automate regular scans across cloud infrastructure to detect vulnerabilities promptly. Leverage tools like Nessus, Qualys, or OpenVAS to identify and prioritize threats efficiently. Automated scanning enhances the speed and accuracy of vulnerability detection, enabling timely remediation actions to bolster cloud security.
Use Cloud-Native Security Services and Features
Leverage built-in security features provided by cloud service providers. Utilize tools like AWS Config, Azure Security Center, or Google Cloud Security Command Center to monitor, analyze, and respond to security threats effectively. Integration of these services strengthens the security posture of cloud environments.
Establish a Comprehensive Vulnerability Management Policy
Develop detailed protocols outlining the vulnerability assessment process, remediation procedures, and responsibilities. Define clear guidelines for vulnerability prioritization, classification, and mitigation strategies. A well-defined policy streamlines vulnerability management efforts, ensuring a structured approach to safeguarding cloud assets.
Foster Collaboration Between Security and DevOps Teams
Encourage cross-functional collaboration to integrate security practices throughout the development and deployment lifecycle. Emphasize communication and cooperation between security and DevOps teams to implement security controls seamlessly. Aligning security objectives with development processes enhances agility and resilience in cloud security practices.
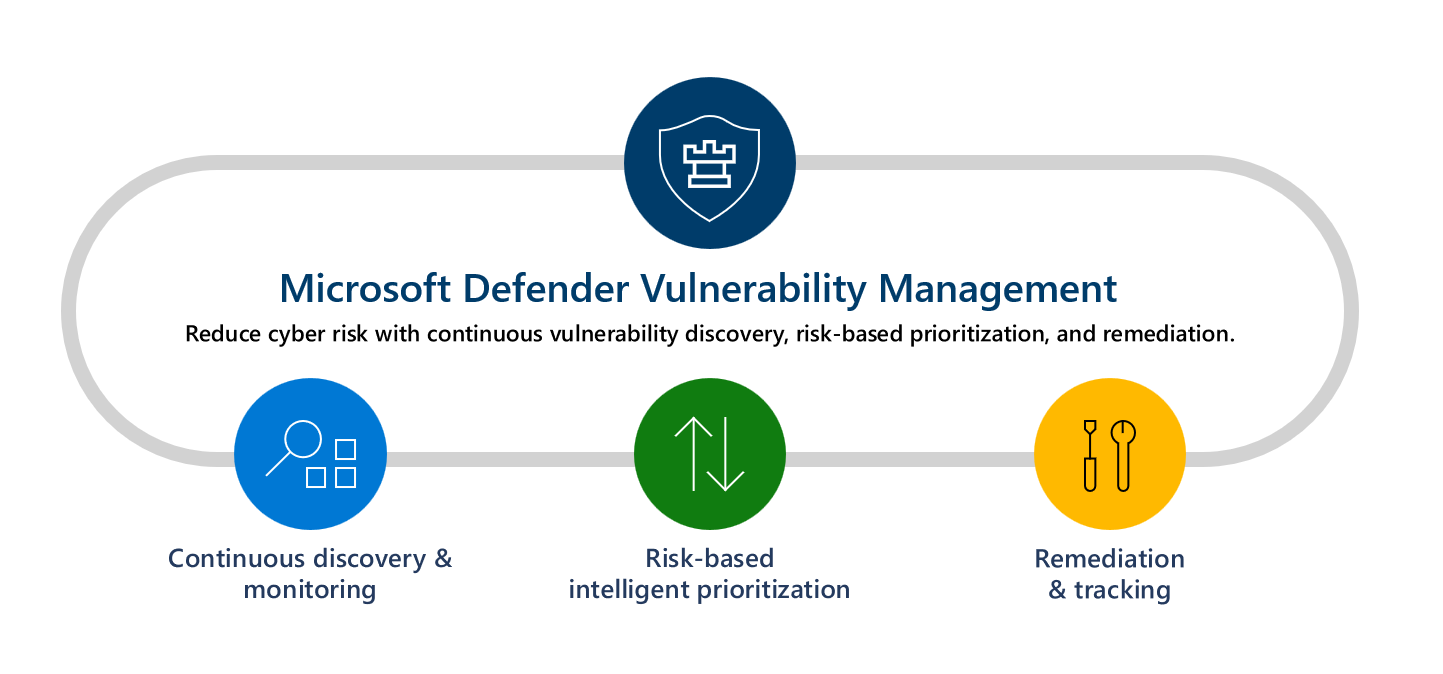
The Cutting-Edge of Cloud Vulnerability Management
Integration of Artificial Intelligence and Machine Learning
The integration of AI and ML in cloud vulnerability management is revolutionizing how threats are detected and mitigated efficiently. By enabling automated threat analysis and response, organizations can proactively address vulnerabilities before they are exploited, enhancing overall security posture. This advanced technology assists in real-time threat detection, minimizing response times to potential attacks.
Cloud-Based Vulnerability Management Platforms
Adopting cloud-based vulnerability management platforms offers dynamic scalability and flexibility, allowing organizations to efficiently manage their security needs across diverse cloud environments. These platforms streamline vulnerability assessments, remediation processes, and compliance monitoring, promoting comprehensive security coverage while optimizing resource utilization. Cloud-native solutions simplify deployment and ensure swift updates for enhanced protection.
Continuous Security Monitoring and Threat Intelligence Sharing
The shift towards continuous security monitoring and threat intelligence sharing fosters a collective defense approach within the cybersecurity community. By actively monitoring cloud environments for anomalies and sharing threat intelligence across platforms, organizations can collectively strengthen their defenses against evolving cyber threats. This collaborative effort enhances incident response capabilities and enables proactive measures to prevent breaches in cloud security.
Incorporating these emerging trends in cloud vulnerability management equips organizations with proactive security measures, enhancing their resilience against sophisticated cyber threats. By embracing AI and ML technologies, leveraging cloud-based platforms, and fostering community-driven security practices, businesses can stay ahead in safeguarding their digital assets within the dynamic cloud landscape.
Advanced Tools and Technologies for Cloud Vulnerability Management
Cloud Security Posture Management (CSPM) Tools
Cloud Security Posture Management (CSPM) tools are essential for continuously monitoring and ensuring compliance with security best practices in cloud environments. These tools provide real-time visibility into cloud infrastructure configurations, flagging misconfigurations and potential risks to prevent security breaches effectively.
Vulnerability Assessment and Penetration Testing (VAPT) Tools
Vulnerability Assessment and Penetration Testing (VAPT) tools play a crucial role in identifying vulnerabilities in cloud systems. Through automated scans and simulated attacks, these tools help organizations proactively detect weaknesses and prioritize remediation efforts to enhance overall security posture.
Security Information and Event Management (SIEM) Systems
Security Information and Event Management (SIEM) systems are integral for aggregating and analyzing security data from various sources within cloud environments. By correlating events and detecting anomalies in real-time, SIEM systems enable swift incident response and enhance threat detection capabilities for proactive risk mitigation.
Cloud-Native Security Services
Cloud-native security services are designed to protect cloud workloads and applications seamlessly. These services offer features like encryption, identity and access management (IAM) controls, and continuous monitoring, ensuring robust security measures tailored to the dynamic nature of cloud environments, thereby safeguarding against evolving cyber threats.