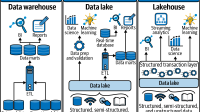
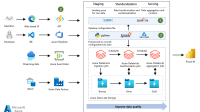
In the digital age, ensuring the privacy and security of cloud data has become paramount. Understanding the key principles, regulations, and best practices of cloud data privacy is crucial for organizations and individuals alike. This comprehensive guide on Cloud data privacy explores the importance of safeguarding data in the cloud, covering essential regulations, tools, and benefits to help you navigate the complex landscape of data protection.

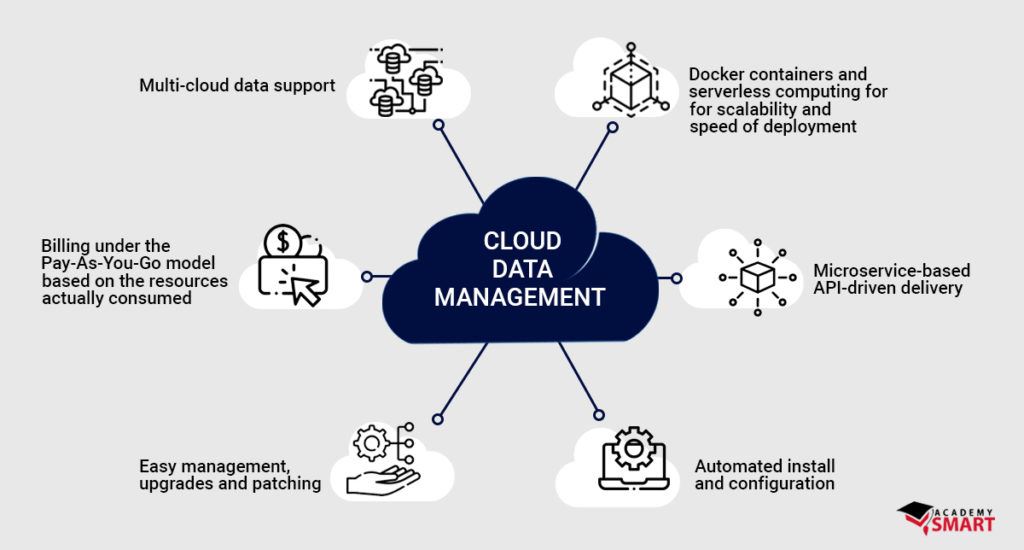
Best Practices for Cloud Data Privacy
Enhancing Security with Strong Passwords and Multi-Factor Authentication
Utilizing strong passwords and implementing multi-factor authentication are fundamental practices in safeguarding cloud data. Strong passwords coupled with additional layers of authentication significantly reduce the risk of unauthorized access, enhancing overall data protection in the cloud environment.
Regular Monitoring of Cloud Data Access and Usage
Continuous monitoring of cloud data access and usage is imperative to detect any suspicious activities promptly. By monitoring user interactions with data stored in the cloud, organizations can identify anomalies or unauthorized access attempts, ensuring data integrity and confidentiality.
Regular Security Audits and Penetration Testing
Conducting regular security audits and penetration testing on cloud systems helps identify vulnerabilities and potential weaknesses in data protection measures. By proactively testing the security infrastructure, organizations can strengthen their defenses, patch vulnerabilities, and mitigate security risks effectively.
Employee Training on Cloud Data Privacy Best Practices
Educating employees on cloud data privacy best practices is critical to maintaining a secure environment. Training programs should focus on data handling protocols, security awareness, and incident response procedures to ensure that staff members understand their roles in upholding data privacy standards.