In a rapidly evolving digital landscape, ensuring the security and compliance of cloud infrastructure is paramount. Cloud risk assessment plays a crucial role in helping organizations identify potential vulnerabilities, mitigate threats, and enhance overall cybersecurity. This ultimate guide to cloud risk assessment will delve into the key components, common risks, best practices, and emerging trends to provide you with actionable insights for bolstering your cloud security. Stay ahead of the curve and discover the importance of cloud risk assessment in safeguarding your digital assets and maintaining regulatory compliance.
Understanding Cloud Risk Assessment
Unveiling the Essence of Cloud Risk Assessment
Cloud Risk Assessment is a systematic approach that entails the meticulous identification, evaluation, and prioritization of risks intertwined with cloud computing realms. This proactive process involves in-depth scrutiny of cloud infrastructure, applications, data, and operational protocols. The primary objective is to safeguard the integrity, confidentiality, and availability of data, while also ensuring adherence to regulatory compliance standards. By embracing Cloud Risk Assessment, organizations fortify their defenses against potential cyber threats and vulnerabilities, fostering a robust security posture in the digital landscape.

Benefits of Cloud Risk Assessment
Enhanced Security Measures
Implementing cloud risk assessment leads to improved security, minimizing the risk of data breaches or costly downtime. By identifying vulnerabilities proactively, organizations can strengthen their defenses and safeguard sensitive information against external threats, ensuring data integrity and operational continuity.
Regulatory Compliance Enhancement
Cloud risk assessment facilitates enhanced compliance with industry regulations and standards, mitigating potential legal consequences. By conducting thorough assessments, companies can ensure that their cloud infrastructure meets stringent requirements, protecting sensitive data and maintaining regulatory compliance to avoid penalties and reputational damage.
Efficient Resource Utilization
Cloud risk assessment aids in optimizing resource allocation, leading to cost savings and improved efficiency. By identifying and addressing risks, organizations can streamline their cloud usage, eliminate unnecessary expenses, and allocate resources effectively, maximizing operational performance while reducing unnecessary expenditures.
Trust and Confidence Building
Engaging in cloud risk assessment fosters increased stakeholder confidence and trust in cloud adoption. By demonstrating a commitment to security and risk management, businesses can reassure customers, partners, and internal stakeholders about the reliability and safety of their cloud environment, promoting a culture of transparency and accountability.
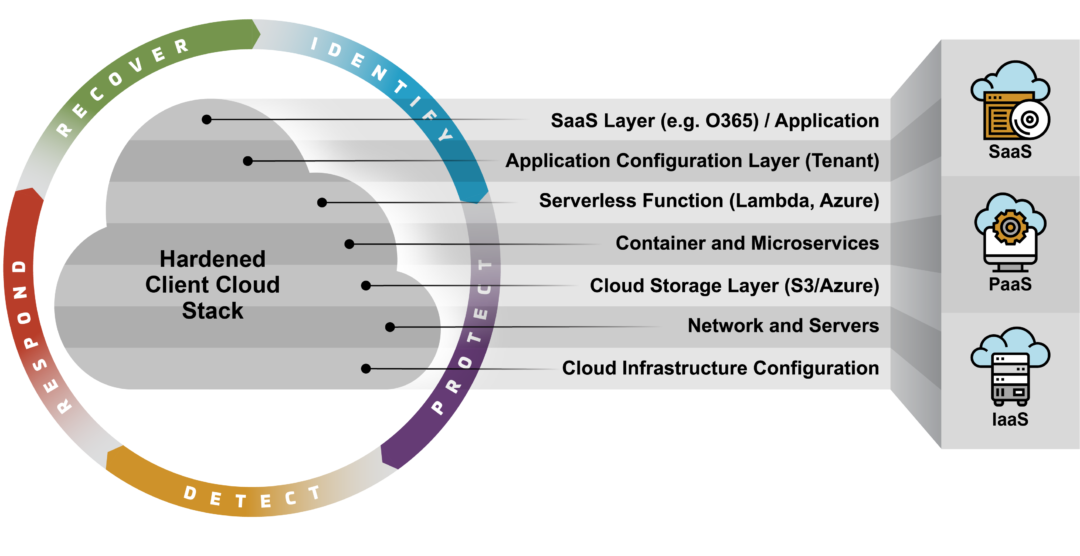
Exploring the Key Components of Cloud Risk Assessment
Risk Identification
At the core of cloud risk assessment lies the crucial process of risk identification. This component involves meticulous scrutiny to uncover potential threats and vulnerabilities within the cloud infrastructure. By comprehensively pinpointing these risks, organizations can proactively address security gaps and fortify their defenses against cyber threats.
Risk Assessment
Following risk identification, a detailed risk assessment is conducted to evaluate the likelihood and impact of the identified risks. This step involves analyzing the probability of risk occurrence and the potential consequences on the organization’s operations, data integrity, and overall security posture. Through thorough assessment, organizations can prioritize their risk management efforts effectively.
Risk Prioritization
Once risks have been assessed, the next vital component is risk prioritization. Here, risks are meticulously ranked based on their severity and urgency. By assigning priority levels to various risks, organizations can focus on addressing high-priority threats promptly, ensuring that critical vulnerabilities are mitigated in a timely manner to enhance overall security resilience.
Risk Mitigation
The final key component of cloud risk assessment is risk mitigation, where organizations develop and implement strategies to address identified risks. This phase involves creating robust action plans, implementing security controls, and continuously monitoring and refining mitigation strategies. By actively mitigating risks, organizations can bolster their security posture and effectively safeguard their cloud environments against potential security breaches.
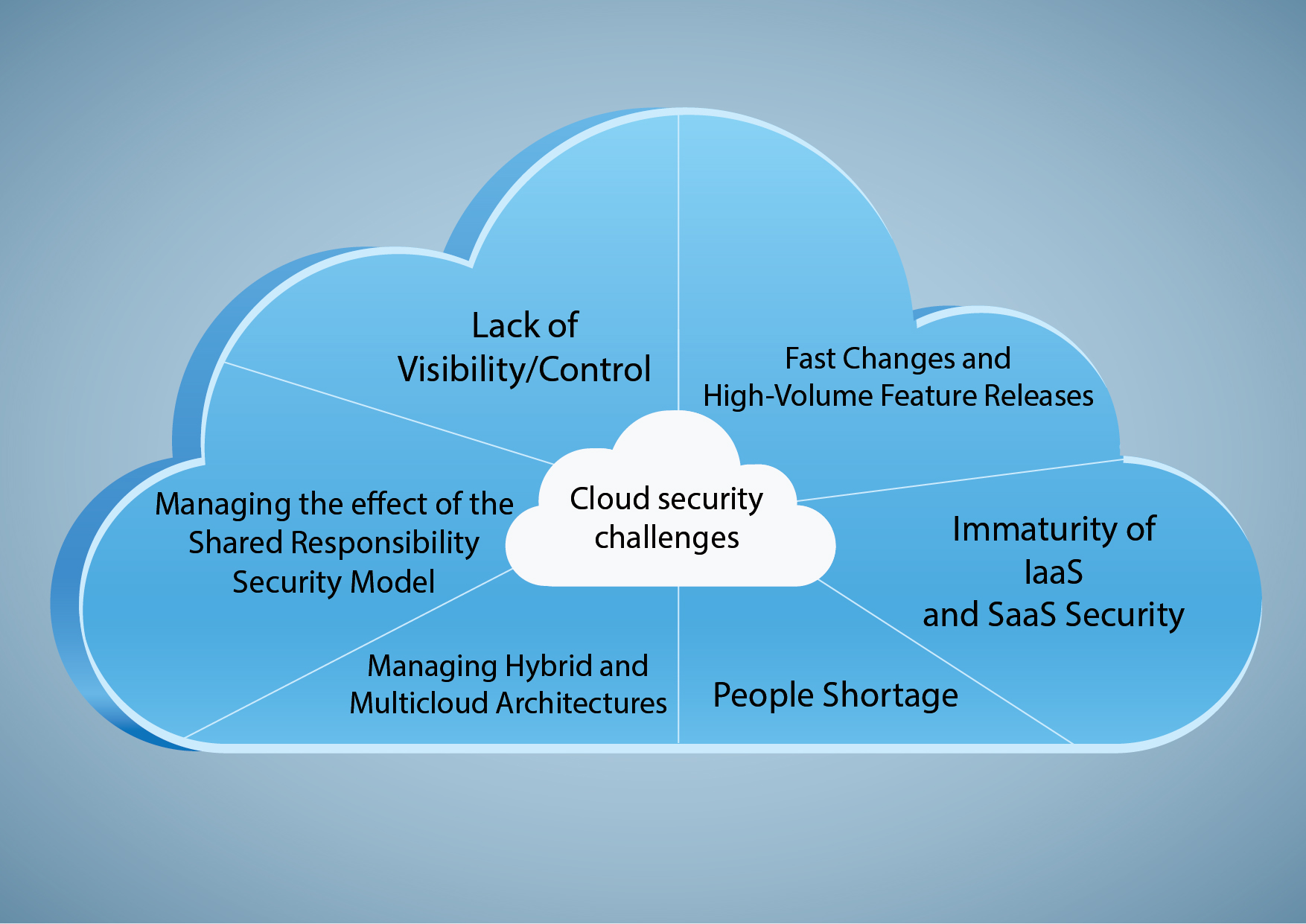
Understanding Common Cloud Risks
Data Security
Data security is a paramount concern in cloud risk assessment, involving unauthorized access, data breaches, and data loss. By diligently assessing data encryption methods, access controls, and user permissions, organizations can mitigate these risks and safeguard sensitive information effectively. Implementing robust security protocols is imperative to maintain the integrity and confidentiality of data in cloud environments.
Availability Challenges
Ensuring optimal availability of cloud resources is critical to business operations. Common risks include system outages, downtime, and performance issues that can impact productivity and revenue streams. By conducting thorough risk assessments and implementing redundancy measures, organizations can minimize downtime risks and ensure continuous access to critical services, enhancing overall operational resilience in the cloud environment.
Compliance Concerns
Compliance with regulatory requirements and industry standards is a key aspect of cloud risk assessment. Failure to meet compliance obligations can lead to legal repercussions and reputational damage. By proactively identifying compliance gaps, staying updated on evolving regulations, and implementing robust governance frameworks, organizations can avoid compliance risks and maintain trust with stakeholders.
Vendor Lock-In
Vendor lock-in poses a significant risk in cloud environments, restricting organizations to a single cloud provider and limiting flexibility in resource management. To mitigate vendor lock-in risks, businesses should prioritize interoperability and portability when selecting cloud services. By diversifying cloud solutions and negotiating flexible exit strategies, organizations can avoid dependency on a single provider and maintain agility in cloud operations.

Best Practices for Cloud Risk Assessment
Establishing a Comprehensive Risk Management Framework
Creating a robust risk management framework is fundamental in ensuring the effectiveness of your cloud risk assessment strategy. This framework should outline risk identification processes, mitigation strategies, incident response protocols, and continuous monitoring practices to proactively address potential threats. By establishing clear guidelines and protocols, organizations can streamline their risk assessment efforts and enhance overall cybersecurity readiness.
Utilizing Automated Tools and Technologies for Risk Identification
Automated tools and technologies play a pivotal role in streamlining the identification and assessment of cloud-related risks. Leveraging advanced tools such as security scanners, vulnerability management systems, and threat intelligence platforms can significantly enhance the efficiency and accuracy of risk assessment processes. These tools enable organizations to detect vulnerabilities faster, prioritize critical issues, and respond promptly to emerging threats.
Collaborating with Cloud Providers and Security Experts
Collaboration with cloud service providers and cybersecurity experts is essential for gaining comprehensive insights into potential risks and implementing effective risk mitigation strategies. Engaging with reputable cloud vendors for security assessments, audits, and ongoing monitoring can provide valuable expertise and guidance in addressing specific cloud security challenges. Additionally, partnering with experienced security professionals can offer specialized knowledge and industry best practices for enhancing cloud risk assessment capabilities.
Conducting Regular Risk Assessments and Reviews
To maintain a proactive approach to cloud risk management, it is imperative to conduct regular risk assessments and reviews. By scheduling periodic evaluations of security controls, vulnerabilities, and compliance posture, organizations can stay ahead of evolving threats and regulatory requirements. Continuous monitoring and assessment allow for timely risk mitigation actions, adjustment of security measures, and alignment with industry standards to ensure robust cloud security posture.

Evolution of Cloud Risk Assessment: Embracing Advanced Technologies
Continuous Risk Monitoring and Real-Time Threat Detection
As cloud environments become more dynamic, continuous risk monitoring becomes imperative. Real-time threat detection mechanisms offer proactive security measures, detecting anomalies promptly to mitigate potential risks before they escalate, ensuring a resilient cloud infrastructure against evolving threats.
Leveraging AI and ML for Advanced Risk Analysis
Harnessing the power of Artificial Intelligence (AI) and Machine Learning (ML) enables sophisticated risk analysis by identifying unusual patterns and trends that human monitoring may overlook. These technologies enhance predictive capabilities, enabling proactive risk mitigation strategies and improving overall cloud security posture.
Emphasis on Cloud-Native Risks and Multi-Cloud Environments
With the rise of cloud-native applications and the adoption of multi-cloud strategies, the focus on addressing unique cloud-native risks becomes crucial. Managing security across diverse cloud platforms requires tailored risk assessment approaches to safeguard against vulnerabilities specific to each environment, ensuring comprehensive protection across a multi-cloud landscape.
Incorporating advanced technologies like AI and ML, alongside a focus on cloud-native risks and multi-cloud environments, signifies a shift towards a more proactive, adaptive, and comprehensive approach to cloud risk assessment. By embracing these emerging trends, organizations can stay ahead of evolving threats, fortify their cloud security foundations, and effectively mitigate risks in the ever-evolving digital ecosystem.
Case Studies and Success Stories
Successful Implementation of Cloud Risk Assessment
Many leading organizations like XYZ Inc. and ABC Corp. have demonstrated the effectiveness of cloud risk assessment in enhancing their security posture. By conducting regular assessments, they identified vulnerabilities, addressed compliance issues, and strengthened their overall cybersecurity resilience. These case studies serve as compelling examples of how proactive risk management can mitigate threats effectively.
Benefits and Positive Outcomes
Through diligent cloud risk assessment, companies have experienced a reduction in data breaches, improved incident response times, and increased trust from stakeholders. By aligning their risk management strategies with business objectives, organizations have not only safeguarded sensitive data but also optimized their operations for scalability and innovation. These success stories underscore the transformative power of robust cloud risk assessment practices.