Are you looking to enhance your business operations with the latest technology trends? Dive into the world of cloud-based applications, where flexibility and scalability meet efficiency and cost-effectiveness. In this article, we will explore the benefits, considerations, and security measures of utilizing cloud-based applications to elevate your business to new heights. Whether you are a small startup or a large enterprise, understanding the ins and outs of cloud-based applications is crucial for staying competitive in today’s digital landscape.
In the process of digital transformation, choosing the right cloud-based application can make all the difference in streamlining your workflow and boosting productivity. With the increasing adoption of cloud solutions, it’s essential to grasp the key factors to consider when selecting the most suitable option for your business needs. From evaluating performance metrics to analyzing cost implications, the process of choosing a cloud-based application can be daunting yet rewarding. Stay tuned as we delve deeper into the world of Cloud-based applications and uncover the secrets to successful implementation and security measures.

Exploring the Essence of Cloud-Based Applications
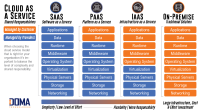
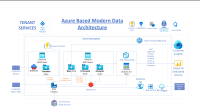
Cloud-based applications revolutionize business operations by residing on remote servers accessible via the internet. Their perks include ubiquitous access, diminished hardware expenditures, and seamless software upgrades. From ubiquitous webmail to collaborative document editors and efficient CRM platforms, examples abound, showcasing the versatility and convenience of cloud-based applications in modern business environments.

Unlocking the Benefits of Cloud-Based Applications
Enhancing Cost-effectiveness
Cloud-Based Applications alleviate the burden of investing in costly hardware and maintaining IT personnel, shifting to a more budget-friendly operational model. By embracing cloud services, businesses can redirect capital into growth initiatives rather than infrastructure expenses, promoting financial efficiency and agility.
Embracing Flexibility and Scalability
One of the hallmark advantages of Cloud-Based Applications is their adaptability to fluctuating workloads. This scalability feature empowers organizations to swiftly adjust IT resources in response to changing demands, ensuring optimal performance without unnecessary overhead costs during peak usage periods.
Fostering Improved Collaboration
Cloud solutions revolutionize teamwork dynamics by enabling seamless real-time document sharing and data collaboration among team members regardless of geographical locations. This enhanced accessibility and connectivity streamline workflows, promoting efficiency and collective productivity within the organization.
Prioritizing Enhanced Security
In the realm of Cloud-Based Applications, data protection is paramount. Robust security protocols implemented by cloud providers bolster data integrity and shield applications from potential cyber threats, offering a secure environment for critical information storage and seamless operations.

Choosing the Right Cloud-Based Application
When selecting a cloud-based application, it’s paramount to analyze your business’s unique needs. Consider the scalability, data storage, and integration requirements tailored to your operations. Evaluating features, functionality, and costs across various applications is crucial. Ensure seamless alignment with your current IT setup and security protocols to avoid compatibility issues. Seek insights from user reviews and recommendations to gain practical perspectives on usability and reliability. Making an informed decision based on these factors will lead to a successful adoption of the right cloud-based application for your business needs.

Implementing Cloud-Based Applications
Planning and Preparation for a Smooth Transition
Implementing cloud-based applications requires meticulous planning. Assess your current IT infrastructure, identify compatibility needs, and allocate resources for a successful transition. Consider scalability, integrations, and data migration strategies to streamline the process seamlessly.
Secure and Efficient Data Migration
Data security is paramount during the migration process. Utilize encryption methods, backup data, and implement secure transfer protocols to safeguard sensitive information. Ensure data integrity post-migration and conduct thorough testing to validate the reliability of the cloud-based application.
Effective User Training and Adoption
Empower your team with thorough training sessions to maximize the benefits of the new cloud application. Provide hands-on workshops, tutorials, and access to support resources to facilitate a smooth transition. User proficiency significantly impacts the application’s productivity and overall success.
Continuous Monitoring and Performance Management
Optimal performance requires continuous monitoring and management. Utilize performance analytics tools to track application usage, identify bottlenecks, and proactively address any performance issues. Regularly update and maintain the application to ensure peak efficiency in your operations.

Enhancing Security Measures for Cloud-Based Applications
Choosing a Trusted Cloud Provider
Selecting a reputable cloud provider with a solid security history is paramount. Look for providers with certifications like ISO 27001 to ensure compliance with international standards, offering peace of mind regarding data protection and confidentiality.
Implementing Multi-Factor Authentication
Enhance security by incorporating multi-factor authentication (MFA) and stringent access controls. MFA adds layers of verification beyond passwords, reducing risks of unauthorized access and fortifying your cloud-based application’s security posture significantly.
Continuous Monitoring and Updates
Stay vigilant against evolving cyber threats by regularly monitoring your cloud environment. Implement timely security updates and patches to address vulnerabilities promptly, safeguarding sensitive data from potential breaches and data leaks.
Data Backup and Recovery Planning
Ensure business continuity by having a robust data backup and recovery strategy. In the event of a security incident, having a comprehensive plan in place minimizes downtime and data loss, helping your business recover swiftly and efficiently.

Cloud-Based Applications in Different Industries
Transforming Industries with Cloud-Based Applications
Cloud-based applications have revolutionized various industries, enhancing efficiency and customer experiences. In healthcare, electronic health records streamline patient management, while telemedicine offers remote care. Financial sectors benefit from online banking’s accessibility and secure mobile payment systems. Education embraces virtual classrooms for interactive learning and streamlined student information systems. In retail, e-commerce platforms optimize sales, inventory systems streamline operations, and CRM tools enhance customer relationships. Cloud-based applications empower industries for seamless operations and improved services.

Emerging Trends Shaping the Future of Cloud-Based Applications
Embracing Advanced Technologies
The future of cloud-based applications is set to witness a surge in the integration of artificial intelligence (AI) and machine learning capabilities. This advancement will enable enhanced automation, predictive analytics, and personalized user experiences, revolutionizing how businesses operate in a data-driven environment.
Convergence of Cloud and IoT
The synergy between cloud-based applications and Internet of Things (IoT) devices will play a pivotal role in shaping future trends. Seamless integration will lead to a more interconnected ecosystem, facilitating real-time data processing, remote monitoring, and efficient decision-making processes across various industries.
Edge Computing and Serverless Architectures
As organizations strive for quicker data processing and reduced latency, the focus on edge computing and serverless architectures within cloud-based applications will intensify. This shift will optimize resource utilization, improve scalability, and enhance overall performance, catering to evolving business needs effectively.
Sustained Emphasis on Security and Compliance
In the ever-evolving digital landscape, security and compliance remain paramount concerns for cloud-based applications. Future trends will emphasize robust security measures, including encryption protocols, identity management, and compliance frameworks to safeguard sensitive data and ensure regulatory adherence in an increasingly interconnected environment.