In the digital age, ensuring robust cloud infrastructure security is paramount for organizations across industries. The ever-evolving landscape of cyber threats highlights the need for efficient best practices and compliance regulations to safeguard sensitive data and maintain operational integrity. This comprehensive guide on Cloud infrastructure security delves into the fundamental principles, emerging trends, and incident response strategies to help businesses navigate the complex realm of cybersecurity in the cloud.
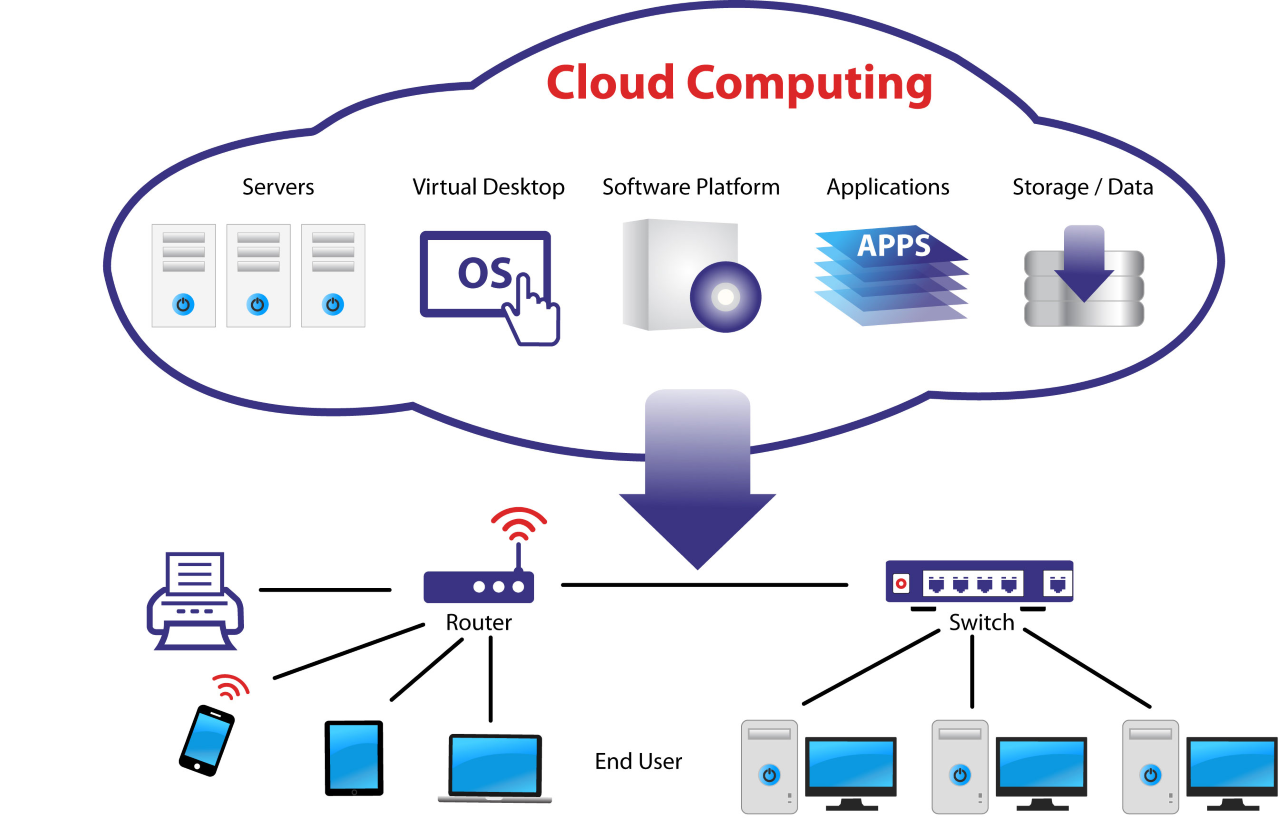
Deep Dive into Understanding Cloud Infrastructure Security
Protecting Vital Components of Cloud Computing
Cloud infrastructure security revolves around safeguarding the core elements of cloud computing like servers, storage, and networks. Ensuring the integrity and availability of these components is critical for the overall security posture of an organization operating in the cloud environment.
Ensuring Data Confidentiality, Integrity, and Availability
Maintaining the confidentiality, integrity, and availability of data stored and processed in the cloud is a foundational aspect of cloud infrastructure security. Implementing robust security protocols not only protects sensitive information but also ensures that it is accessible to authorized users when needed.
Implementing Essential Security Measures
Employing a combination of security measures like encryption, access controls, and intrusion detection systems is imperative in fortifying cloud infrastructure security. Encryption secures data in transit and at rest, while access controls restrict unauthorized entry, and intrusion detection systems identify and respond to potential threats promptly.
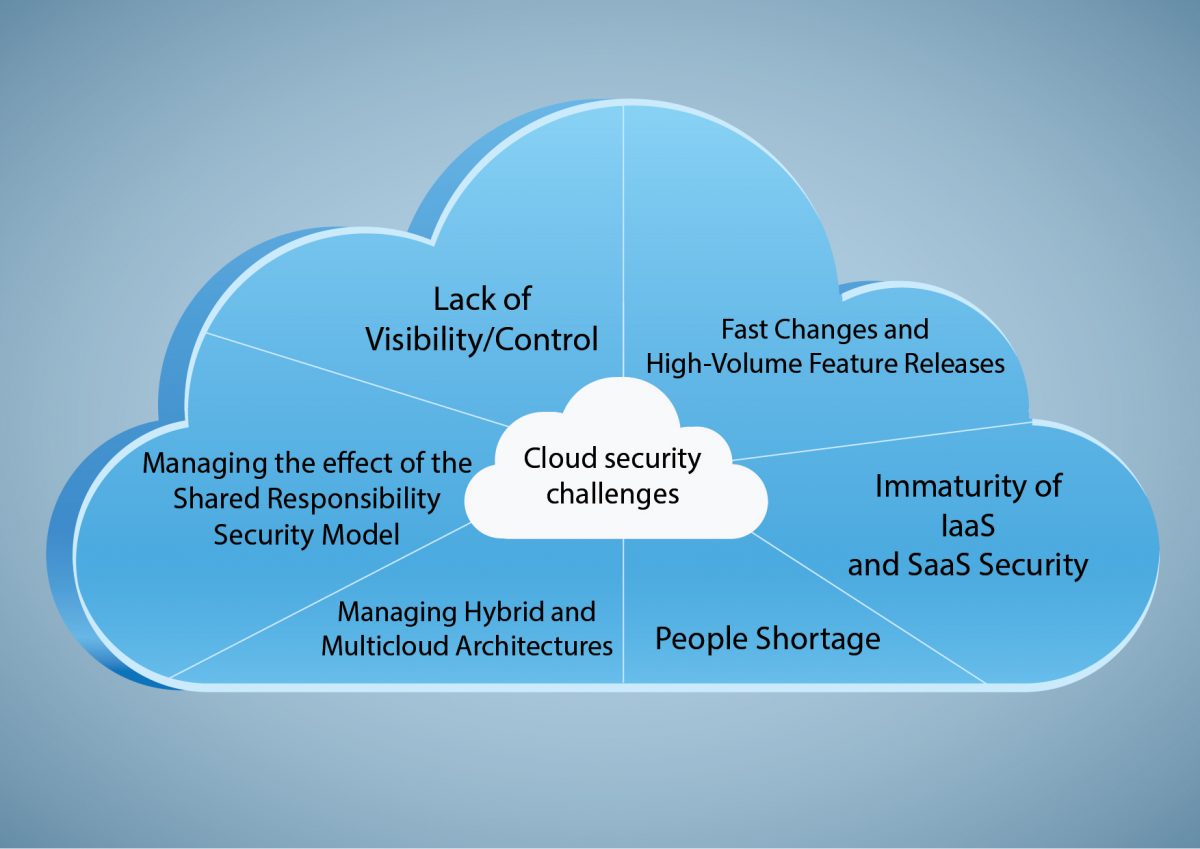
Navigating Cloud Security Compliance and Regulations
Comprehensive Compliance Landscape
Various industries face stringent compliance regulations concerning cloud infrastructure security. From healthcare (HIPAA) to financial services (PCI DSS) and data protection (GDPR), organizations must adhere to specific rules to safeguard sensitive data and maintain trust.
Upholding Regulatory Standards
Organizations are obligated to ensure their cloud infrastructure aligns with established compliance regulations. Compliance entails implementing robust security measures, conducting regular audits, and promptly addressing any deviations to maintain a secure environment. Failure to comply can result in severe penalties and reputational damage.
Tailoring Security Measures
To meet compliance requirements, organizations must tailor their security measures to address the nuances of each regulation. This includes encryption protocols, access controls, data retention policies, and incident response procedures tailored to the specific demands of HIPAA, PCI DSS, GDPR, and other relevant regulations.
Continuous Monitoring and Adaptation
Maintaining compliance with evolving regulations demands continuous monitoring and adaptation of security practices. Organizations must stay vigilant, keep abreast of changes in compliance frameworks, and adjust their cloud security strategies accordingly to ensure ongoing alignment with regulatory standards. Regular updates and staff training are essential components of this continuous compliance effort.
Common Cloud Infrastructure Security Threats
Understanding the Landscape
In the realm of cloud infrastructure security, common threats like data breaches, malware attacks, and denial-of-service assaults loom large. Awareness is key; organizations must acknowledge these risks and enforce robust security solutions to defend their cloud ecosystems effectively.
Mitigating Vulnerabilities
One essential defense strategy is the regular patching and updating of software within cloud environments. This practice helps close off potential entry points for cyber attackers, reducing the likelihood of successful intrusions and data breaches. Implementing this measure is critical for maintaining a secure cloud infrastructure.
Proactive Security Measures
Preventing cloud security threats requires a proactive approach. By integrating stringent access controls, monitoring network traffic, and enhancing encryption protocols, organizations can fortify their defenses against evolving cyber threats. Stay ahead by prioritizing continuous security assessments and threat intelligence to safeguard your cloud infrastructure effectively.
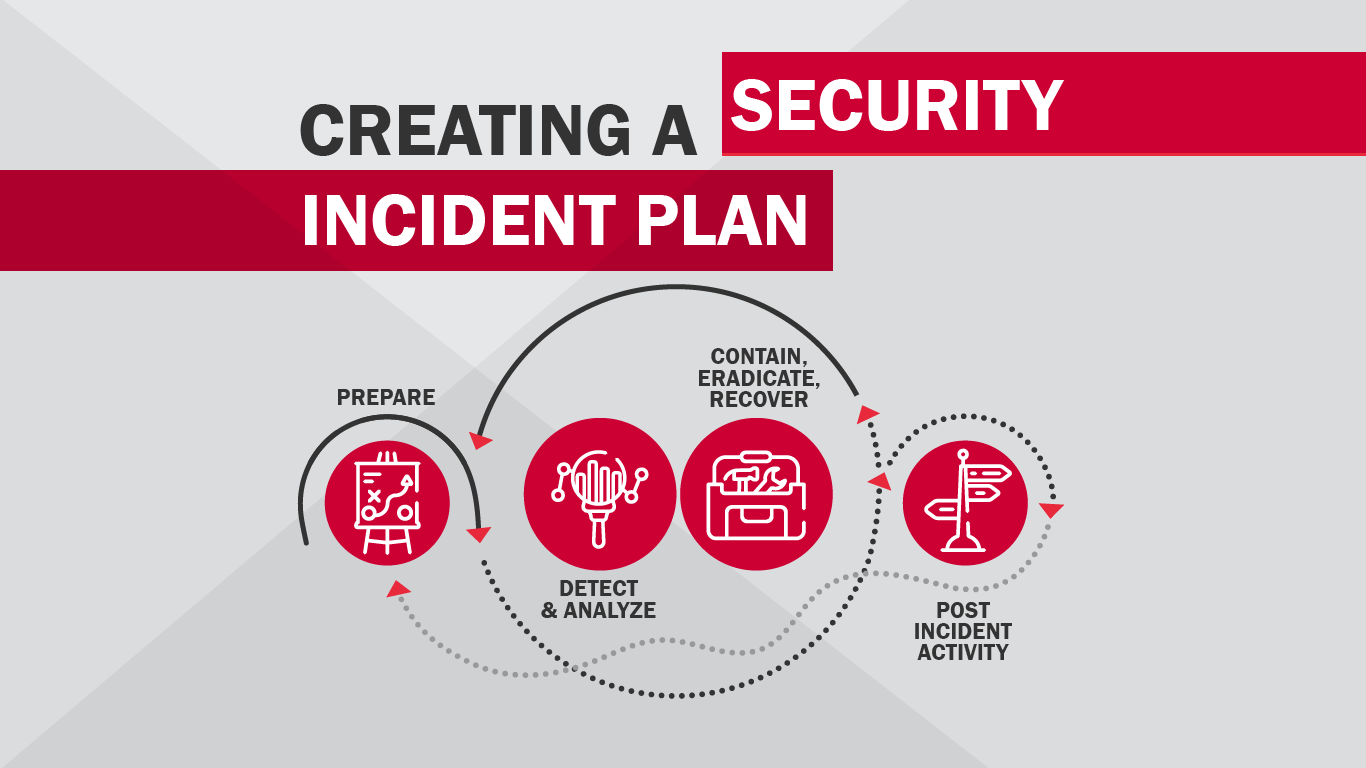
Strategies for Effective Cloud Infrastructure Security Incident Response
Importance of Incident Response Planning
Having a well-defined plan for responding to security incidents is imperative in safeguarding cloud infrastructure. This proactive approach ensures a swift and organized response, minimizing potential damages from breaches. Incident response plans should be regularly reviewed and updated to align with evolving threats and technologies.
Comprehensive Incident Response Steps
An effective incident response plan should encompass key stages such as containment, eradication, and recovery. Containment involves isolating the affected systems to prevent further spread of the incident. Eradication focuses on removing the root cause of the security breach, while recovery aims at restoring normal operations with minimal disruption.
Emphasizing Personnel Training
Regular security training for personnel is a cornerstone of successful incident response in cloud infrastructure security. Employees must be equipped with the knowledge and skills to identify, report, and respond to security incidents promptly. Training programs should cover threat awareness, incident detection, and proper escalation procedures to bolster overall cybersecurity readiness.
By integrating these best practices into your cloud infrastructure security incident response strategy, organizations can effectively mitigate risks and enhance their overall cybersecurity posture in the ever-evolving digital landscape. Proactive planning, thorough response procedures, and continuous employee training are essential pillars in safeguarding sensitive data and ensuring operational resilience against potential threats.