As an experienced SEO writer, your task is to write two opening paragraphs in English for an article titled Ultimate Guide to Cloud Security Best Practices: Key Elements & Trends. This article targets the keyword Cloud security measures. The meta description for this article is:
Learn about the best practices, key elements, and emerging trends in cloud security to safeguard your data and infrastructure. Discover the importance of implementing cloud security measures.
The opening paragraphs should be designed to grab the reader’s attention and encourage them to continue reading the article. Use the meta description as a guide to determine what information to include in the opening paragraphs. Each paragraph should not exceed 200 characters.
In writing the opening paragraphs, make sure to adhere to the following writing guidelines:
– Intent: Provide a comprehensive guide on cloud security best practices, trends, and challenges
– Style: Informative and educational
– Tone: Professional
Also, be sure to include the keyword Cloud security measures in one of the paragraphs. Additionally, provide some background or context about the article topic to help readers understand what they will be reading.
Deep Dive into Understanding Cloud Security and Its Importance
Cloud security measures are pivotal in safeguarding cloud infrastructure, data, and applications against cyber threats and unauthorized access. The importance lies in upholding data privacy, compliance adherence, and averting reputation harm. Employing a multi-layered security strategy encompasses network security, data protection, identity management, and threat detection to fortify cloud environments effectively. Maintaining a robust cloud security posture is indispensable for modern enterprises to mitigate risks and ensure operational continuity.
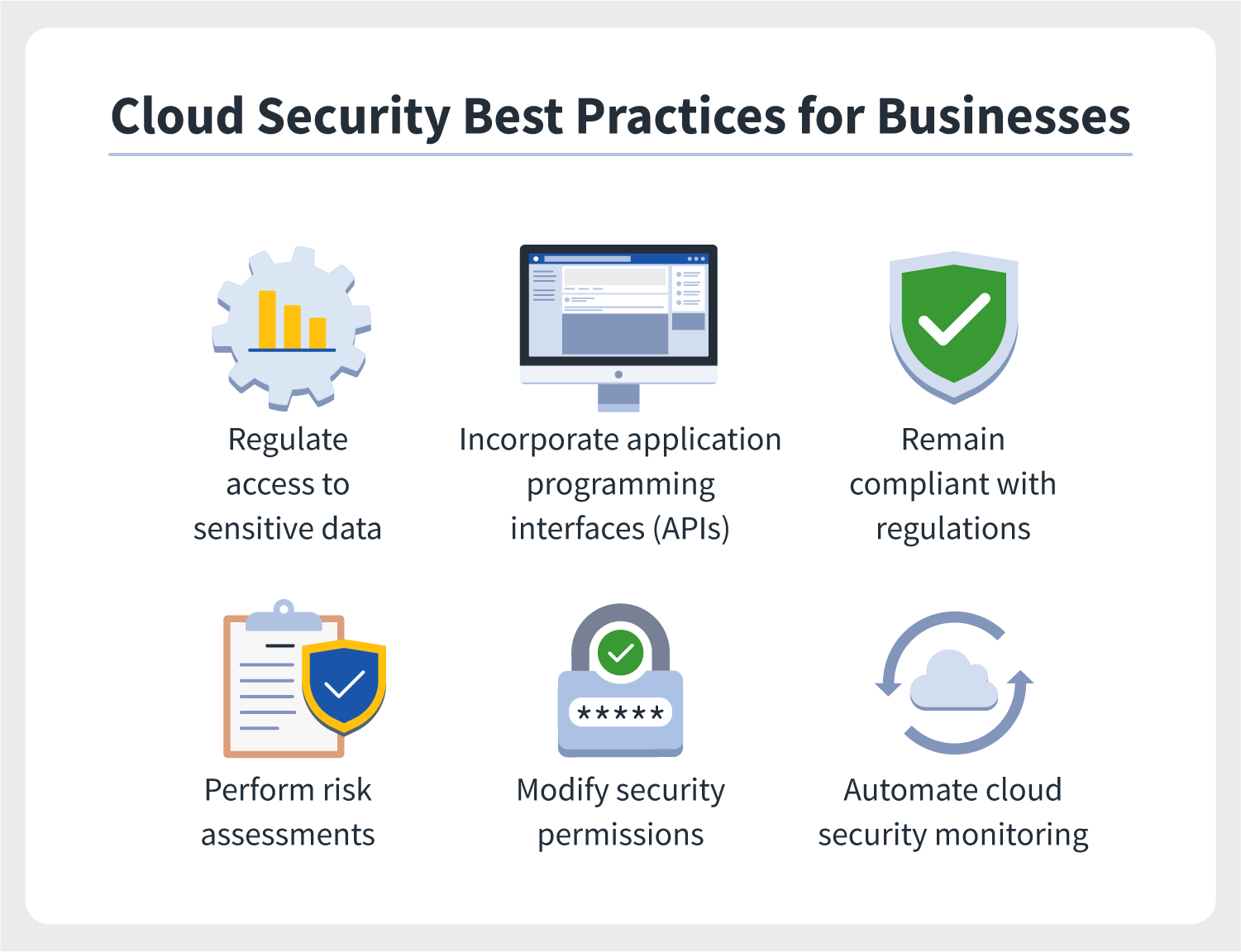
Implementing Cloud Security Best Practices
Implementing robust Cloud Security Best Practices is paramount in safeguarding sensitive data and infrastructure. Here are key strategies to enhance your cloud security posture:
Control User Access with IAM
Implement Identity and Access Management (IAM) protocols to control user privileges effectively. IAM ensures only authorized personnel have access to critical resources, reducing the risk of data breaches.
Strengthen Network Security
Configure firewalls and implement network segmentation to restrict unauthorized access. These measures enhance data protection by creating barriers against malicious entities, fortifying your cloud environment.
Data Encryption for Enhanced Security
Encrypt data at rest and in transit to safeguard sensitive information from unauthorized access. Encryption adds an extra layer of security, rendering data indecipherable to unauthorized parties, mitigating potential risks.
Continuous Monitoring and Auditing
Regularly monitor and audit your cloud infrastructure for any suspicious activities or vulnerabilities. Proactive monitoring helps identify and address security issues promptly, ensuring a secure cloud environment.
Detect and Respond to Threats
Implement intrusion detection and prevention systems to swiftly detect and respond to security threats. These systems analyze network traffic, identify anomalies, and take immediate actions to mitigate potential risks, bolstering overall security measures.
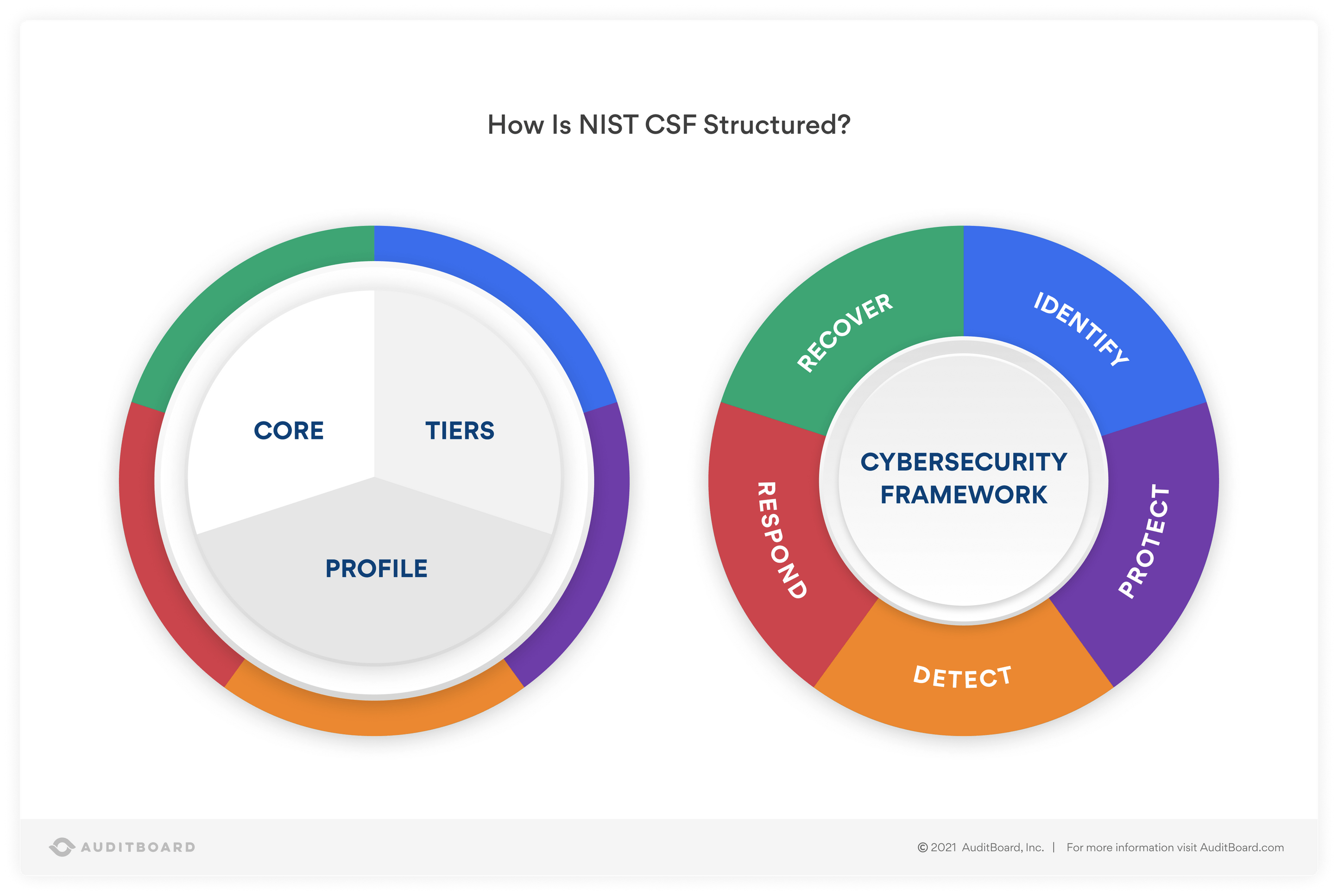
Cloud Security Standards and Compliance
Maintaining robust cloud security involves adhering to industry-recognized standards like ISO 27001 and NIST CSF. Compliance not only showcases commitment to security but also bolsters overall defense strategies. Additionally, meeting regulatory mandates such as GDPR and HIPAA is imperative for businesses dealing with sensitive data, promoting trust and legal conformity.
Regularly reviewing and updating security policies and procedures is vital to keep pace with evolving threats and comply with changing regulations. This continuous evaluation ensures that cloud security measures remain effective, addressing new challenges and reinforcing resilience against potential vulnerabilities. By staying proactive and vigilant in compliance efforts, organizations can significantly enhance their security posture and safeguard critical assets.

Emerging Innovations in Cloud Security Trends
Cloud security is rapidly evolving with innovative trends shaping the future of data protection.
Cloud-Native Security Solutions
Cloud-native security tools are tailored for cloud infrastructures, providing robust safeguards and streamlined operations, ensuring data integrity and resilience against cyber threats.
AI and ML Integration
Integration of Artificial Intelligence and Machine Learning in cloud security enhances threat detection accuracy and automates responses, proactively mitigating risks and strengthening overall defense mechanisms.
Zero-Trust Security Principles
Zero-trust models revolutionize security by scrutinizing and continuously verifying access requests, diminishing the risk of unauthorized infiltrations irrespective of user location, providing granular security controls.
Container Security Advancements
Container security tools are crucial for safeguarding containerized applications and workloads in cloud environments, ensuring isolation and protection against vulnerabilities, bolstering overall cloud security postures.

Benefits of Implementing Cloud Security Measures
Implementing robust cloud security measures offers a myriad of benefits, starting with improved data protection. By leveraging advanced security protocols and encryption techniques, organizations can significantly reduce the risk of data breaches, safeguarding sensitive information from unauthorized access.
Furthermore, adhering to industry regulations and standards is simplified through cloud security practices, enhancing compliance efforts. This not only mitigates legal risks but also instills trust in customers, showcasing a commitment to data privacy, thereby fostering trust and confidence in cloud services.
In addition, a well-structured cloud security framework minimizes downtime and business disruptions stemming from security incidents. Proactive security measures ensure quick response and resolution, maintaining business continuity and safeguarding critical operations effectively.
Moreover, implementing cloud security best practices leads to cost savings by optimizing security infrastructure. Mitigating security risks reduces the likelihood of financial losses associated with cyber incidents, enabling organizations to allocate resources efficiently and focus on business growth and innovation.