Understanding Cloud Service Security: Best Practices, Threats, and Tools is a crucial topic in today’s digital landscape. In this article, we will delve into the essential aspects of cloud service security, including best practices, common threats, compliance protocols, and the latest tools available to secure cloud environments. With the increasing reliance on cloud services for data storage and processing, the need for robust security measures has never been more pressing. Stay tuned to discover the key strategies for ensuring the safety and integrity of your data in the cloud.
In the realm of information technology, ensuring Cloud service security is paramount for protecting sensitive data and safeguarding against cyber threats. As organizations continue to migrate their operations to cloud-based platforms, it is essential to understand the importance of implementing comprehensive security measures. By staying informed about the best practices, emerging trends, and effective tools for enhancing cloud security, businesses can proactively mitigate risks and strengthen their defense against potential security breaches. Stay informed and empower your organization with the knowledge to secure your cloud infrastructure effectively.

Exploring the Essence of Cloud Service Security
Cloud service security stands as the fortress safeguarding data, applications, and infrastructure within the realms of cloud computing. Its significance lies in thwarting unauthorized access, data breaches, and diverse security menaces. The shared responsibility model delineates a pivotal understanding where cloud providers secure the platform, while clients bear the onus of safeguarding data and applications. This model underscores the collaborative effort in upholding robust cloud security protocols.

Best Practices for Cloud Security
In the realm of Cloud Service Security, implementing robust access controls is paramount. Incorporating multi-factor authentication and role-based access ensures only authorized personnel can access sensitive data, reducing the risk of unauthorized breaches. By enforcing strong access mechanisms, organizations can fortify their cloud environments against potential security threats effectively.
Continuous monitoring and scanning of cloud infrastructures are essential best practices for Cloud Service Security. Regular assessments help identify vulnerabilities and potential threats promptly, allowing for timely mitigation actions. By staying vigilant and proactive in monitoring the cloud environment, organizations can prevent security incidents and maintain a secure infrastructure for their data storage and processing needs.
Encrypting data both in transit and at rest is a fundamental practice to safeguard information in cloud environments. Encryption adds an additional layer of protection, ensuring that even if data is intercepted, it remains unreadable and secure. By employing encryption protocols, organizations can enhance the confidentiality and integrity of their data, mitigating the risks of data breaches and unauthorized access.
Utilizing cloud-native security tools and services offered by cloud providers is a strategic approach to bolstering cloud security measures. These specialized tools are designed to integrate seamlessly with cloud environments, providing enhanced protection and visibility into security incidents. By leveraging these advanced security solutions, organizations can enhance their overall security posture and better defend against evolving cyber threats in the cloud.

Common Cloud Security Threats
Data Breaches and Vulnerabilities
Data breaches in cloud services often result from weak access controls or vulnerabilities in applications. Hackers exploit these weaknesses to gain unauthorized access to sensitive information, posing a significant threat to data integrity and confidentiality. Implementing robust access control mechanisms and regularly updating applications are essential steps to mitigate these risks in cloud environments.
DDoS Attacks on Cloud Infrastructure
Distributed Denial of Service (DDoS) attacks pose a severe threat to cloud infrastructure and applications by flooding them with overwhelming traffic, leading to service disruptions. By targeting the availability of cloud resources, attackers aim to disrupt operations and compromise the reliability of cloud services. Employing DDoS mitigation strategies and monitoring tools are crucial defenses against such attacks.
Malware Infections in Cloud Systems
Malware infections can rapidly spread through cloud-based systems, compromising data security and system integrity. Attackers deploy malicious software to exploit vulnerabilities in cloud environments, potentially leading to data loss or unauthorized access. Regular security assessments, implementing anti-malware solutions, and enforcing strict security protocols are essential in safeguarding against malware threats.
Phishing Scams Targeting Cloud Users
Phishing scams are a prevalent threat targeting cloud users to deceive them into disclosing sensitive information such as login credentials or financial data. Cybercriminals craft deceptive emails or messages to trick users into compromising security unwittingly. Educating users about identifying phishing attempts, implementing multi-factor authentication, and conducting regular security awareness training are vital in combating such threats in cloud environments.

Ensuring Compliance and Regulations in Cloud Service Security
Adherence to Industry Standards
In the realm of Cloud Service Security, it is imperative for organizations to comply with industry-specific regulations like HIPAA, GDPR, and PCI DSS. Adhering to these standards ensures that sensitive data is protected and privacy laws are upheld, bolstering trust with clients and stakeholders.
Certification for Enhanced Trust
Obtaining certifications such as ISO 27001 and SOC 2 showcases a commitment to compliance and security in cloud environments. These certifications validate that robust security measures are in place, instilling confidence in clients regarding the safety of their data.
Evolving Security Policies
To maintain compliance in Cloud Service Security, it is vital to regularly assess and update security policies and procedures. Keeping abreast of evolving regulations and compliance requirements allows organizations to adapt swiftly, minimizing risks and ensuring continued adherence to the latest security standards.

Exploring Cloud Security Tools and Technologies
Enhancing Security with Advanced Solutions
Intrusion detection and prevention systems (IDS/IPS) play a pivotal role in safeguarding cloud environments by actively monitoring and blocking malicious activities in real-time. These advanced systems help identify unauthorized access attempts and potential threats, providing a proactive defense mechanism against cyber intrusions.
Web Application Firewalls (WAFs) serve as a critical line of defense against web-based attacks, offering protection by filtering and monitoring HTTP traffic between web applications and users. By analyzing and blocking malicious HTTP requests, WAFs mitigate the risks associated with common web vulnerabilities, ensuring a secure online presence for cloud services.
Cloud Access Security Brokers (CASBs) act as gatekeepers, managing and controlling access to cloud services and data. These tools offer visibility into cloud usage, enforce security policies, and facilitate compliance across multiple cloud platforms, ensuring secure interactions and data protection within cloud environments.
Data Loss Prevention (DLP) solutions are paramount in preventing sensitive data leakage by monitoring and controlling data transfers across networks. By implementing granular policies, encryption, and content inspection capabilities, DLP solutions help organizations identify, monitor, and protect sensitive information, preventing data breaches and ensuring regulatory compliance in cloud settings.

Continuous Monitoring and Incident Response
In the realm of Cloud Service Security, establishing a robust process for continuous monitoring is crucial. By continuously monitoring cloud environments, organizations can swiftly detect and respond to security incidents in a timely manner, minimizing the impact of potential threats. This proactive approach enhances overall security posture and helps mitigate risks effectively.
A well-defined incident response plan is essential for effective Cloud Service Security. Organizations should develop a detailed plan outlining roles, responsibilities, and predefined procedures for addressing security breaches promptly. Having a structured incident response framework in place enables swift and coordinated actions in the event of a security incident, enhancing incident response efficiency and reducing downtime.
Regular security audits and penetration testing are vital components of a comprehensive Cloud Service Security strategy. By conducting periodic audits and penetration tests, organizations can evaluate the effectiveness of their security measures, identify vulnerabilities, and proactively address any weaknesses in their cloud security posture. This proactive approach helps organizations stay ahead of evolving threats and strengthens their overall security resilience.
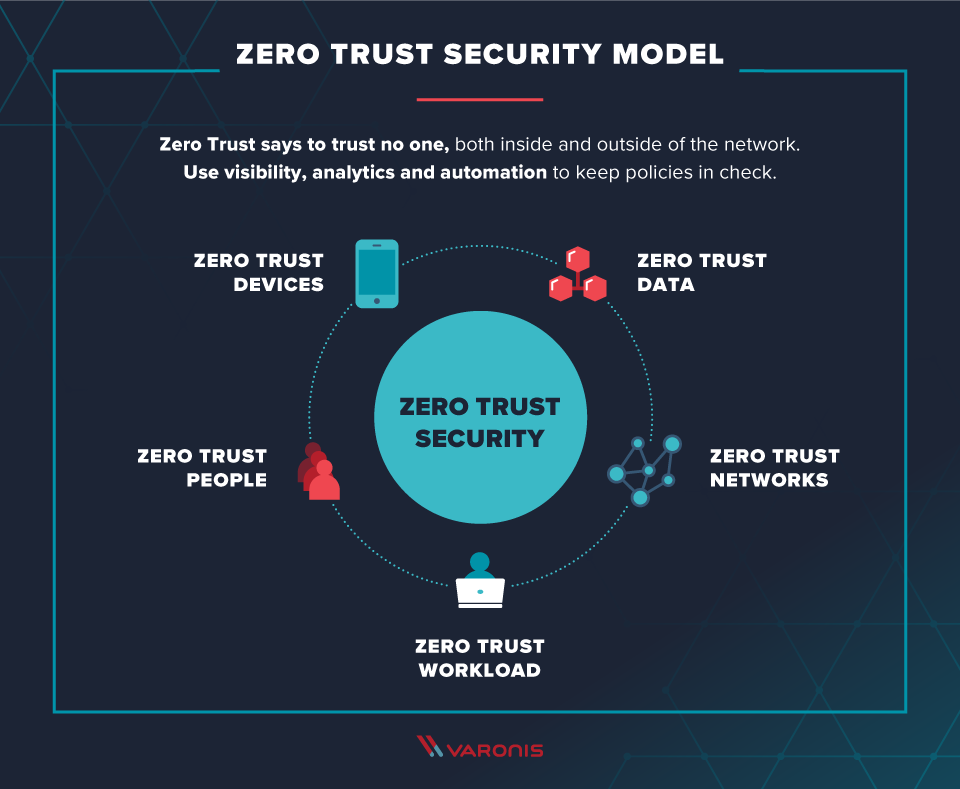
Evolving Trends in Cloud Security
Zero-Trust Principles
The adoption of zero-trust principles marks a revolutionary shift in cloud security paradigms. By assuming no implicit trust, every access request is verified, minimizing breach impacts and enhancing overall security robustness. Implementing zero-trust frameworks ensures a proactive defense strategy vital in today’s dynamic threat landscape, offering granular control and visibility over cloud service security.
AI and ML Integration
The integration of artificial intelligence (AI) and machine learning (ML) technologies is reshaping cloud security by enabling advanced threat detection and intelligent response mechanisms. Leveraging AI and ML algorithms enhances anomaly detection, predictive analytics, and automated incident response in real-time, fortifying cloud environments against sophisticated cyber threats with unparalleled efficiency.
Cloud-Native Security Tools
With the digital transformation accelerating, the industry is witnessing a surge in cloud-native security tools and services specifically designed to address the unique security challenges of cloud environments. These tools offer tailored protection mechanisms, such as container security, serverless security, and cloud workload protection, ensuring comprehensive coverage and heightened resilience in safeguarding cloud service security.
